WordPress 6.5.2 was released yesterday, on April 9, 2024. It included a single security patch, along with a handful of bug fixes. The security patch was for a Stored Cross-Site Scripting vulnerability that could be exploited by both unauthenticated users, when a comment block is present on a page, and by authenticated users who have access to the block editor such as contributors.
All Wordfence users are protected against exploits targeting this vulnerability through unauthenticated methods. Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability through authenticated methods on April 10, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on May 10, 2024.
The patch has been backported to version 6.1 and later of WordPress. We urge all WordPress users to verify that their sites are updated to 6.5.2, or another backported security release, immediately as this issue could allow full site takeover when the right conditions are met. Most sites should have auto-updated, however, it’s a good idea to verify the auto-update was successful.
Affected Versions: 6.5 – 6.5.1, 6.4 – 6.4.3, 6.3 – 6.3.3, 6.2 – 6.2.4, 6.1 – 6.1.5, 6.0 – 6.0.7
CVE ID: N/A
CVSS Score: 7.2 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:N
Researcher/s: John Blackbourn, stealthcopter
Fully Patched Version: 6.1.6, 6.2.5, 6.3.4, 6.4.4, 6.5.2
In version 6.0, WordPress added a new Avatar block. This block can be used to display a post author’s avatar within a post or to show a comment author’s avatar when used inside a comment block. Unfortunately, the code used to display a link to an author’s supplied website URL or post archive was insecurely implemented making it possible to inject arbitrary JavaScript using an attribute-based XSS payload.
$label = 'aria-label="' . sprintf( esc_attr__( '(%s author archive, opens in a new tab)' ), $author_name ) . '"';
And this highlights the affected code for the comment author’s name:
$label = 'aria-label="' . sprintf( esc_attr__( '(%s website link, opens in a new tab)' ), $comment->comment_author ) . '"';
The core of the issue here is that esc_attr() is performed prior to sprintf(). This means that the comment_author and author_name values are not escaped prior to being included into the HTML because the value is simply a placeholder until sprintf() runs.
We discovered and reported on a similar issue present in a plugin and theme in the past.
As with any Cross-Site Scripting vulnerability, this can be leveraged to inject malicious web scripts that can be used to add administrative users or modify theme/plugin code to inject a backdoor, along with many other consequences. While this is severe, it is worth noting that only sites that allow contributor-level and higher registration and provide access to the block editor, along with sites using a comment block, are affected.
Further, this serves as an important reminder to verify that the order of operations is as intended and desired when sanitizing and escaping data along with formatting the data.
Wordfence Firewall
The following demonstrates how the Wordfence firewall will block malicious attempts to exploit this vulnerability.
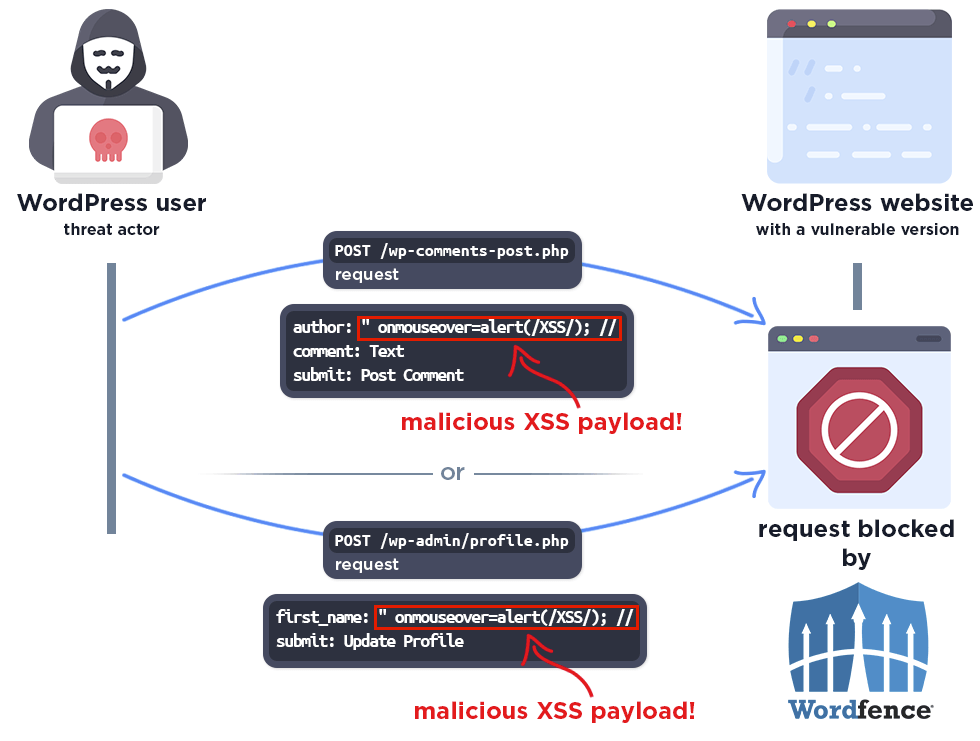
Conclusion
In today’s post, we analyzed a patch for a Stored Cross-Site Scripting vulnerability that was patched in version 6.5.2 of WordPress, and backported to 6.1. This vulnerability can be exploited by both unauthenticated and authenticated users under varying circumstances and be leveraged to inject malicious web scripts into pages. While most sites should automatically update to a patched version of WordPress, we strongly recommend manually checking your site to ensure that it is updated.
All Wordfence users are protected against exploits targeting this vulnerability through unauthenticated methods. Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability through authenticated methods on April 10, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on May 10, 2024.
We recommend sharing this advisory with everyone you know who uses WordPress, as this is a potentially critical issue that could lead to complete site takeover with the right conditions.
Did you know that Wordfence has a Bug Bounty Program? We’ve recently increased our bounties by 6.25x until May 27th, 2024, with our bounties for the most critical vulnerabilities reaching $10,000 USD! If you’re an aspiring or current vulnerability researcher, click here to sign up.
The post Unauthenticated Stored Cross-Site Scripting Vulnerability Patched in WordPress Core appeared first on Wordfence.



