The Wordfence Threat Intelligence team has been monitoring a sudden increase in attack attempts targeting Kaswara Modern WPBakery Page Builder Addons. This ongoing campaign is attempting to take advantage of an arbitrary file upload vulnerability, tracked as CVE-2021-24284, which has been previously disclosed and has not been patched on the now closed plugin. As the plugin was closed without a patch, all versions of the plugin are impacted by this vulnerability. The vulnerability can be used to upload malicious PHP files to an affected website, leading to code execution and complete site takeover. Once they’ve established a foothold, attackers can also inject malicious JavaScript into files on the site, among other malicious actions.
All Wordfence customers have been protected from this attack campaign by the Wordfence Firewall since May 21, 2021, with Wordfence Premium, Care, and Response customers having received the firewall rule 30 days earlier on April 21, 2021. Even though Wordfence provides protection against this vulnerability, we strongly recommend completely removing Kaswara Modern WPBakery Page Builder Addons as soon as possible and finding an alternative as it is unlikely the plugin will ever receive a patch for this critical vulnerability. We are currently protecting over 1,000 websites that still have the plugin installed, and we estimate that between 4,000 and 8,000 websites in total still have the plugin installed.
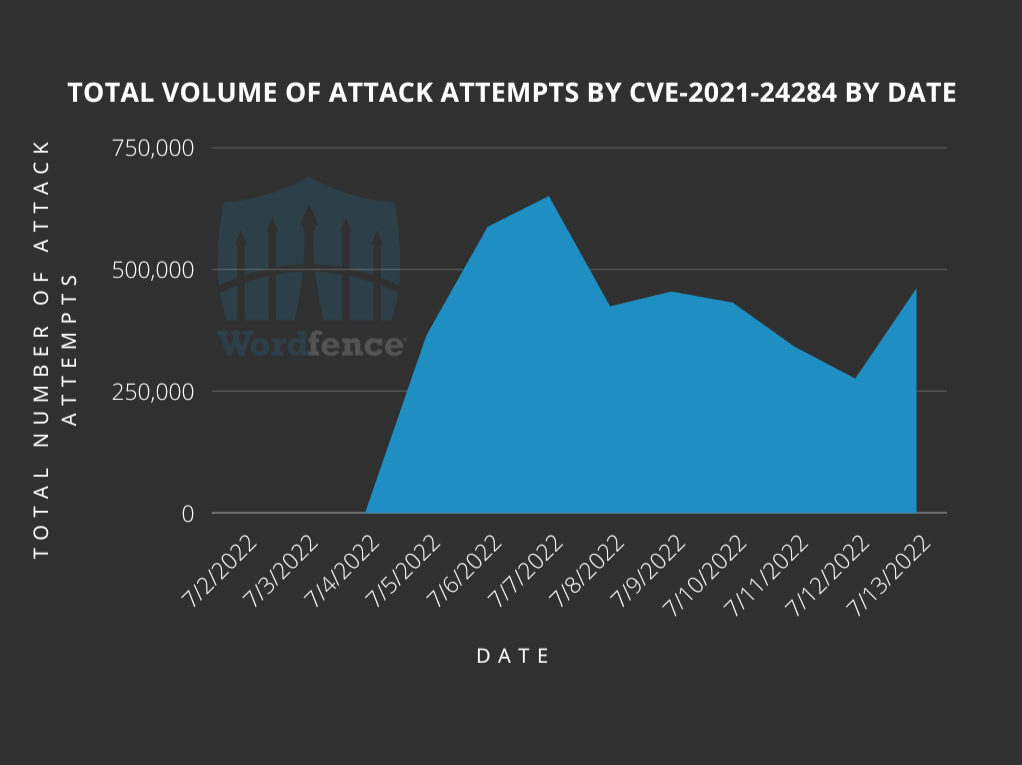
We have blocked an average of 443,868 attack attempts per day against the network of sites that we protect during the course of this campaign. Please be aware that while 1,599,852 unique sites were targeted, a majority of those sites were not running the vulnerable plugin.
Affected Plugin: Kaswara Modern WPBakery Page Builder Addons
Plugin Slug: kaswara
Affected Versions: <= 3.0.1
CVE ID: CVE-2021-24284
CVSS Score: 10.0 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Fully Patched Version: NO AVAILABLE PATCH.
Indicators of Attack
The majority of the attacks we have seen are sending a POST request to /wp-admin/admin-ajax.php using the uploadFontIcon AJAX action found in the plugin to upload a file to the impacted website. Your logs may show the following query string on these events:
/wp-admin/admin-ajax.php?action=uploadFontIcon HTTP/1.1
We have observed 10,215 attacking IP addresses, with the vast majority of exploit attempts coming from these top ten IPs:
- 217.160.48.108 with 1,591,765 exploit attempts blocked
- 5.9.9.29 with 898,248 exploit attempts blocked
- 2.58.149.35 with 390,815 exploit attempts blocked
- 20.94.76.10 with 276,006 exploit attempts blocked
- 20.206.76.37 with 212,766 exploit attempts blocked
- 20.219.35.125 with 187,470 exploit attempts blocked
- 20.223.152.221 with 102,658 exploit attempts blocked
- 5.39.15.163 with 62,376 exploit attempts blocked
- 194.87.84.195 with 32,890 exploit attempts blocked
- 194.87.84.193 with 31,329 exploit attempts blocked

Indicators of Compromise
Based on our analysis of the attack data, a majority of attackers are attempting to upload a zip file named a57bze8931.zip. When attackers are successful at uploading the zip file, a single file named a57bze8931.php will be extracted into the /wp-content/uploads/kaswara/icons/ directory. The malicious file has an MD5 hash of d03c3095e33c7fe75acb8cddca230650. This file is an uploader under the control of the attacker. With this file, a malicious actor has the ability to continue uploading files to the compromised website.
The indicators observed in these attacks also include signs of the NDSW trojan, which injects code into otherwise legitimate JavaScript files and redirects site visitors to malicious websites. The presence of this string in your JavaScript files is a strong indication that your site has been infected with NDSW:
;if(ndsw==
Some additional filenames that attackers are attempting to upload includes:
- [xxx]_young.zip where [xxx] varies and typically consists of 3 characters like ‘svv_young’
- inject.zip
- king_zip.zip
- null.zip
- plugin.zip
What Should I Do If I Use This Plugin?
All Wordfence users, including Free, Premium, Care, and Response, are protected from exploits targeting this vulnerability. However, at this time the plugin has been closed, and the developer has not been responsive regarding a patch. The best option is to fully remove the Kaswara Modern WPBakery Page Builder Addons plugin from your WordPress website.
If you know a friend or colleague who is using this plugin on their site, we highly recommend forwarding this advisory to them to help keep their sites protected, as this is a serious vulnerability that can lead to complete site takeover.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both of these products include hands-on support in case you need further assistance.
The post PSA: Sudden Increase In Attacks On Modern WPBakery Page Builder Addons Vulnerability appeared first on Wordfence.



