On February 15, 2021, our Threat Intelligence team initiated the responsible disclosure process for a vulnerability that we discovered in User Profile Picture, a WordPress plugin installed on over 60,000 sites. The vulnerability made it possible for authenticated users with the upload_files capability to obtain sensitive user information.
We initially reached out to Cozmoslabs, the plugin’s vendor, on February 15, 2021 through their contact form. On February 17, 2021 Cozmoslabs confirmed the inbox for handling discussion and we sent over the full disclosure details. Just a day later we received a response from the plugin’s original developer along with a proposed patch for us to test. We confirmed the patch was adequate and provided an additional security recommendation. They released the patch the same day on February 18, 2021. We highly recommend updating to the fully patched version, 2.5.0, immediately.
Wordfence Premium users received a firewall rule to protect against any exploit attempts targeting this vulnerability on February 15, 2021. Sites still using the free version of Wordfence will receive the same protection on March 17, 2021.
Affected Plugin: User Profile Picture
Plugin Slug: metronet-profile-picture
Affected Versions: <= 2.4.0
CVE ID: Pending.
CVSS Score: 6.5 (Medium)
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N
Fully Patched Version: 2.5.0
User Profile Picture is a plugin designed to allow site owners to upload profile pictures for individual users. By default, WordPress will set a users profile picture to the associated Gravatar, if present, for any given email. This plugin makes it so that user profile pictures can be customized and can override the Gravatar associated with an email address.
One feature the plugin offered was the ability to add user profiles to a post using a Gutenberg block. When adding the block to a post, the plugin made a request for user data to retrieve the users profile picture and username for users with access to the Gutenberg editor in order to add the information to the block. To retrieve this information, the plugin registered the REST API route /mpp/v2/get_users tied to the rest_api_get_users function.
register_rest_route(
'mpp/v2',
'/get_users',
array(
'methods' => 'POST',
'callback' => array( $this, 'rest_api_get_users' ),
'permission_callback' => array( $this, 'rest_get_users_permissions_callback' ),
)
Unfortunately, this REST API endpoint returned more information than was required for its functionality. This included password hashes, hashed user activation keys, usernames, emails, and other less sensitive information.
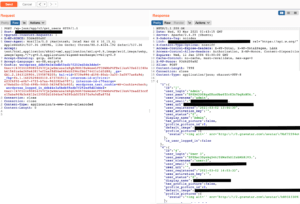
A look at the User Profile Picture exploit.
The REST API endpoint did have a permissions callback preventing users from accessing it unless they had the upload_files capability. By default this would only be available to users in the author role and above. However, the User Profile Picture plugin page promotes a separate plugin, Profile Builder, by the same developers, noting that it can be used to allow other roles to upload images. By doing so, a site owner would make it possible for users and roles that do not have the upload_files capability by default to upload their own profile photos. It is likely that a number of site owners have granted this capability to lower-level users.
In a normal configuration, all authors and editors could retrieve this sensitive information. In addition, any sites where the upload_files capability had been granted to lower-privileged users could be exploited by those users to retrieve this information as well.
If an attacker were able to crack a password or user activation key, then they could potentially log into the vulnerable WordPress site and effectively take it over. However, it should be noted that WordPress passwords and user activation keys are salted and hashed with strong cryptography and, therefore, would be very hard to crack for further use, especially if strong passwords are being used.
Disclosure Timeline
February 15, 2021 – Conclusion of the plugin analysis that led to the discovery of the vulnerability. We develop a firewall rule to protect Wordfence customers and release it to Wordfence Premium users. We made our initial contact attempt with the vendor, CozmosLabs.
February 17, 2021 – We receive a response confirming appropriate inbox for handling discussion. We provide full disclosure details.
February 18, 2021 – We receive an acknowledgement from Ronald Huereca, the original plugin developer, along with a proposed fix. We verify that the fix addresses the security issue and provide an additional security recommendation.
February 18, 2021 – A patched version of the plugin is released as version 2.5.0. We verify again that the vulnerability has been patched.
March 17, 2021 – Free Wordfence users will receive firewall rule.
Conclusion
In today’s post, we detailed a flaw in the User Profile Picture plugin that granted attackers the ability to obtain sensitive information like hashed user passwords. This flaw has been fully patched in version 2.5.0. We recommend that users immediately update to the latest version available, which is version 2.5.0 at the time of this publication.
Wordfence Premium users received a firewall rule protecting against this vulnerability on February 15, 2021, while those still using the free version of Wordfence will receive the same protection on March 17, 2021.
If you know a friend or colleague who is using this plugin on their site, we highly recommend forwarding this advisory to them to help keep their sites protected.
Special thanks to Ronald Huereca, the original developer of the plugin, for working promptly to get a patch out to customers.
The post Medium Severity Vulnerability Patched in User Profile Picture Plugin appeared first on Wordfence.



