On December 18, 2023, right before the end of Holiday Bug Extravaganza, we received a submission for a Local File Inclusion vulnerability in Shield Security, a WordPress plugin with more than 50,000+ active installations. It’s important to note that this vulnerability is limited to just the inclusion of PHP files, however, it could be leveraged by an attacker who has the ability to upload PHP files but can not directly access those files to execute.
Props to hir0ot who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $938.00 for this discovery during our Bug Bounty Program Extravaganza.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those still using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Directory Traversal and Local File Inclusion protection.
We contacted the Shield Security Team on December 21, 2023, and received a response on December 23, 2023. After providing full disclosure details, the developer released a patch on December 23, 2023. We would like to commend the Shield Security Team for their prompt response and timely patch, which was released on the same day.
We urge users to update their sites with the latest patched version of Shield Security, which is version 18.5.10, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Shield Security – Smart Bot Blocking & Intrusion Prevention Security
Plugin Slug: wp-simple-firewall
Affected Versions: <= 18.5.9
CVE ID: CVE-2023-6989
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: hir0ot
Fully Patched Version: 18.5.10
Bounty Awarded: $938.00
The Shield Security – Smart Bot Blocking & Intrusion Prevention Security plugin for WordPress is vulnerable to Local File Inclusion in all versions up to, and including, 18.5.9 via the render_action_template parameter. This makes it possible for an unauthenticated attacker to include and execute PHP files on the server, allowing the execution of any PHP code in those files.
Technical Analysis
Shield Security is a WordPress website security plugin that offers several features to stop attackers, protect and monitor the website, including a firewall, malware scanner and also logs activities.
The plugin includes a template management system that renders .twig, .php or .html files. Unfortunately, the insecure implementation of the plugin’s file template including and rendering functionality allows for arbitrary file inclusion in vulnerable versions. The template path is set with the setTemplate() function.
public function setTemplate( $templatePath ) {
$this->template = $templatePath;
if ( property_exists( $this, 'sTemplate' ) ) {
$this->sTemplate = $templatePath;
}
return $this;
}
The renderPhp() function in the Render class uses the path_join() function to join the template file. It then checks that the template file is an existing file and includes it.
private function renderPhp() :string {
if ( count( $this->getRenderVars() ) > 0 ) {
extract( $this->getRenderVars() );
}
$template = path_join( $this->getTemplateRoot(), $this->getTemplate() );
if ( Services::WpFs()->isFile( $template ) ) {
ob_start();
include( $template );
$contents = ob_get_clean();
}
else {
$contents = 'Error: Template file not found: '.$template;
}
return (string)$contents;
}
Examining the code reveals that there is no file path sanitization anywhere in these functions. This makes it possible to include arbitrary PHP files from the server.
The file inclusion is limited to PHP files in the vulnerability. This means that threat actors cannot exploit one of the most popular remote code execution methods via a log file poisoning attack. Since the plugin also uses isFile() function to file checking, the other popular remote code execution method using wrappers attack is also not possible. Nevertheless, the attacker has several options to include and exploit a malicious PHP file and execute on the server. This can be achieved by chaining the attack and exploiting vulnerabilities in other plugins. However, it’s worth mentioning that the attack possibilities are limited. This would likely be leveraged in an instance where an attacker has access to upload a PHP file, but does not have direct access to the file to execute it.
Wordfence Firewall
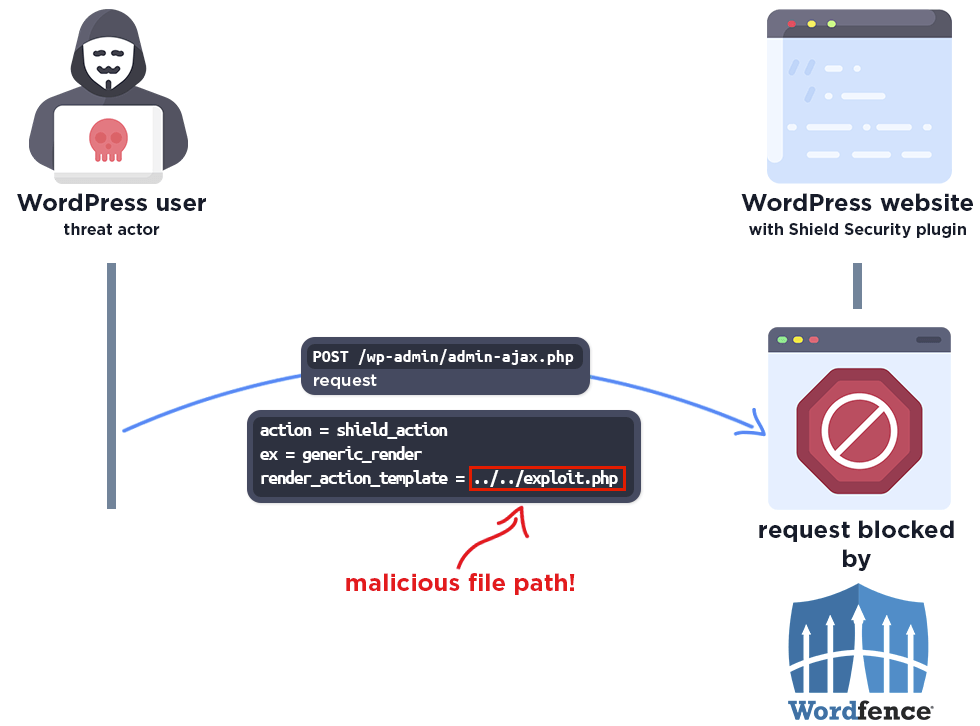
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious file path and blocks the request.
Disclosure Timeline
December 18, 2023 – We receive the submission of the Local File Inclusion vulnerability in Shield Security via the Wordfence Bug Bounty Program.
December 20, 2023 – We validate the report and confirm the proof-of-concept exploit.
December 21, 2023 – We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
December 23, 2023 – The vendor confirms the inbox for handling the discussion.
December 23, 2023 – We send over the full disclosure details. The vendor acknowledges the report and begins working on a fix.
December 23, 2023 – The fully patched version of the plugin, 18.5.10, is released.
Conclusion
In this blog post, we detailed a Local File Inclusion vulnerability within the Shield Security plugin affecting versions 18.5.9 and earlier. This vulnerability allows unauthenticated threat actors to include and execute PHP files on the server, allowing the execution of any PHP code in those files, which can be used for complete site compromise. The vulnerability has been fully addressed in version 18.5.10 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Shield Security.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those still using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Directory Traversal and Local File Inclusion protection.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post Local File Inclusion Vulnerability Patched in Shield Security WordPress Plugin appeared first on Wordfence.