Winter brings a number of holidays in a short period of time, and many organizations shut down or run a skeleton crew for a week or more at the end of the year and beginning of the new year. This makes it easier for would-be attackers to find success as systems are not as closely monitored. This means that during major holidays it is not uncommon to see spikes in attack attempts.
We observed spikes in attack traffic for two of our firewall rules over the Christmas and New Year holidays, which are discussed in more detail below. The spikes in these rules look rather different when compared to each other. What they have in common is that the best defenses are proactively securing your website and keeping WordPress core, themes, and plugins updated.
Targeted Spikes: Downloads Manager Plugin
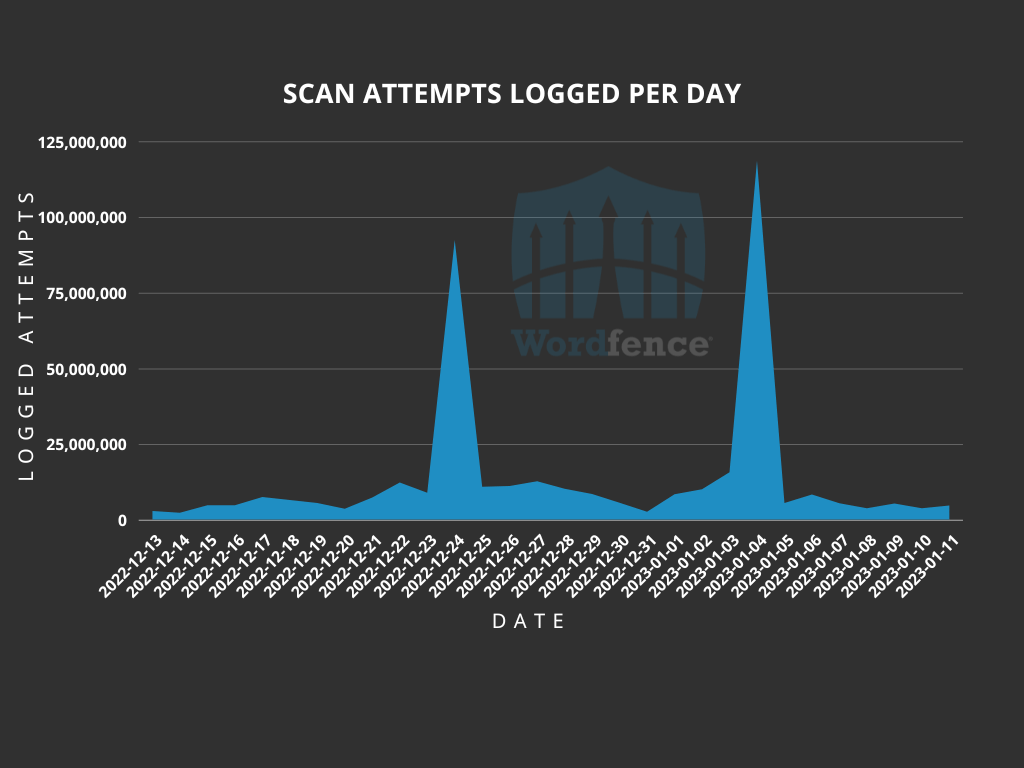
There were two spikes specifically targeting the Downloads Manager plugin by Giulio Ganci. The first spike was on December 24, 2022, with a second spike on January 4, 2023. In the 30-day reporting period, only 17 attempts to scan for readme.txt or debug.log files did not target the Downloads Manager plugin. On average, the rule that blocks these scans typically blocks an average of 7,515,876 scan attempts per day. The first spike saw 92,546,995 scan attempts, and the second spike soared to 118,780,958 scan attempts in a single day.
Over the reporting period, we tracked 466,827 attacking IP addresses. These IP addresses attempted to exploit vulnerabilities on 2,663,905 protected websites. The top 10 IP addresses were responsible for 90,693,836 exploit attempts over the course of the reporting period.
The observed user-agent strings were largely known legitimate user-agents, though some appear to have been modified. The top ten user-agents accounted for 306,845,888 of the total exploit attempts during this time period.
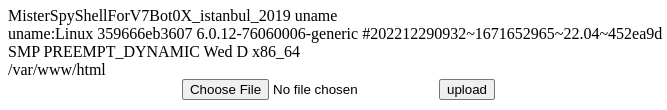
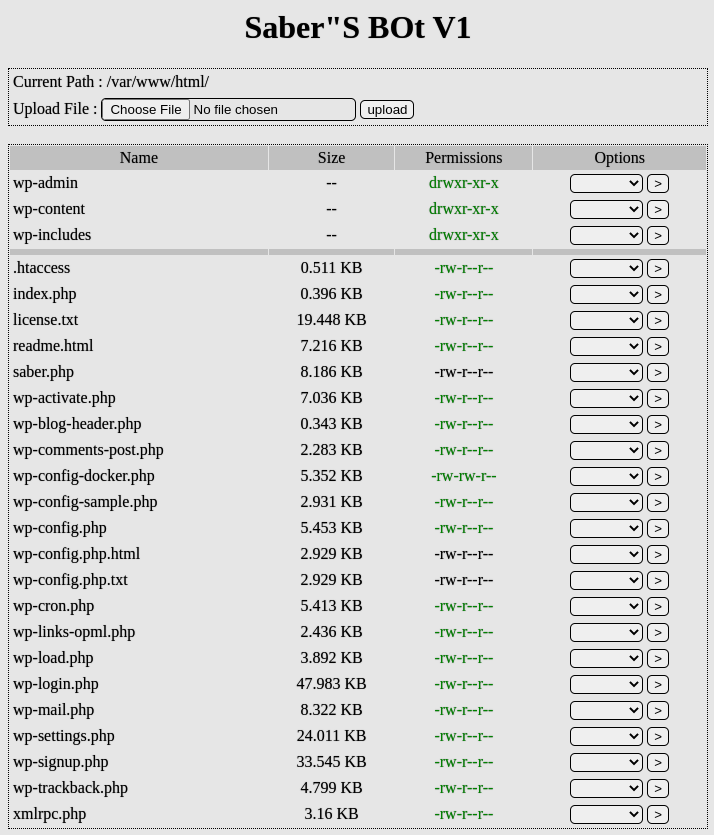
During these spikes, the scans were specifically looking for readme.txt files within the /wp-content/plugins/downloads-manager/ directory of the website. When found, they are primarily attempting to upload the Mister Spy Bot V7 shell with a filename similar to up__jpodv.php, where the last five characters of the name are random letters, or the Saber BOT V1 shell with a filename of saber.php as the malicious payload.
The vulnerability would-be attackers are attempting to exploit is an arbitrary file upload vulnerability found in Downloads Manager <= 0.2. A lack of adequate validation made it possible for files to be uploaded and run on a vulnerable website. This could lead to remote code execution on some sites. The vulnerability was publicly published in 2008, and was never patched. The plugin has since been closed and is no longer available. If this plugin is still being used, it should be removed immediately. Take note that this is not the WordPress Download Manager plugin by W3 Eden, which is still actively being developed and should simply be kept updated with the latest releases as they are published.
Mister Spy Bot V7
The Mister Spy shell returns some basic information about the operating system the website is running on, and the location of the site root on that system, and allows for files to be uploaded. In addition to these features, Mister Spy payloads typically include a reverse shell that allows a successful attacker to obtain additional information about the content management system being used on the website, install additional shells, deface the website, register malicious users on the website, and collect configuration details, among other features.
Saber BOT V1
Saber BOT gives a successful attacker the ability to view files, and modify their permissions and filenames, as well as edit or delete the files. The current path is displayed in the web interface, and an upload form is provided as well. While not as sophisticated as Mister Spy Bot V7, Saber BOT V1 can still lead to remote code execution due to the file upload capabilities.
Untargeted Spikes: Known User-Agents
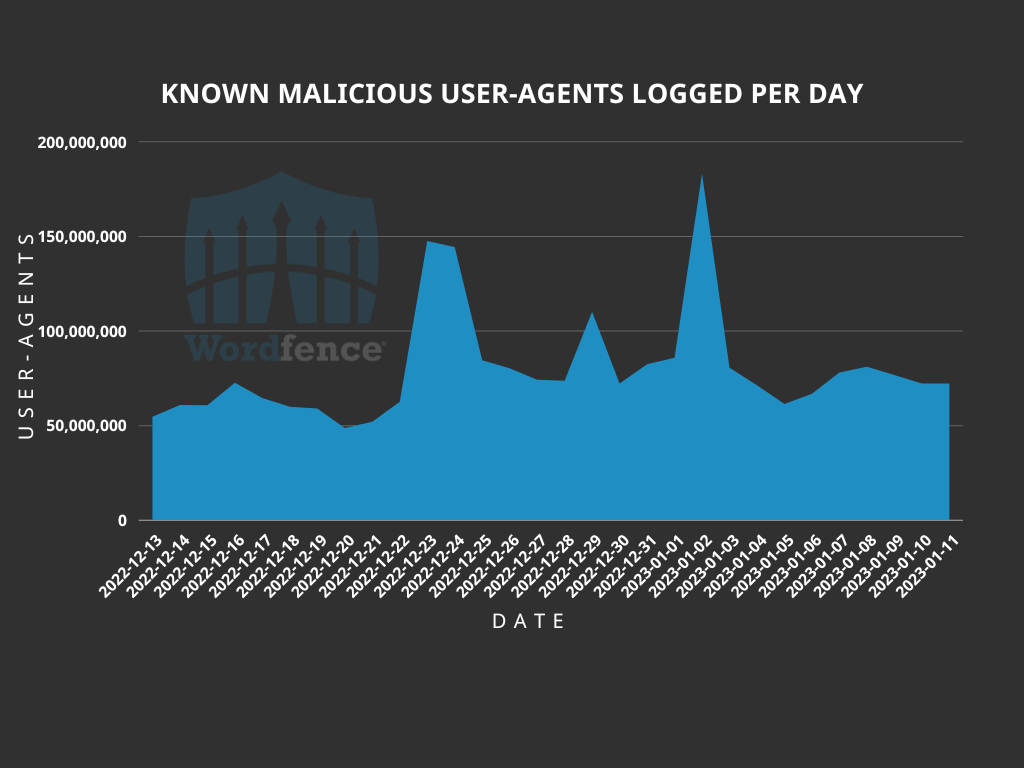
The attack attempts we saw that did not target a specific plugin were blocked due to the use of known malicious user-agent strings. These spikes were not as pronounced as the targeted spikes we saw and occurred on slightly different days. The total number of blocked attacks rose beginning on December 22, 2022, and stayed slightly higher throughout the remainder of the reporting period. Within this time we also saw three spikes on December 23rd and 24th, December 29th, and January 2nd. The January 2, 2023 peak was the largest peak, reaching 183,097,778 blocked attack attempts. This put the peak at nearly three times as many attempts as the average of 66,669,317 blocked per day.
The attack attempts blocked by this firewall rule were much more varied, and did not show an increase in specific payloads or intrusion vectors. Instead, the increase appears to have been a simple rise in the volume of attack attempts across all attack types from actors using known malicious user-agents. One of the most common attack types blocked for using a known malicious user-agent string is probing for hidden webshells.
Cyber Observables
The following observables can be used in conjunction with other indicators as an indication that a compromise may have occurred.
Filenames
The filename for Mister Spy Bot V7 follows a pattern of up__xxxxx.php, where xxxxx is replaced with a random set of five lowercase letters. Saber BOT V1 was consistently named saber.php in these spikes.
- up__jpodv.php
- up__bxyev.php
- up__izlxc.php
- saber.php
Top Ten IP Addresses Targeting Downloads Manager
- 158.69.23.79
- 109.248.175.80
- 20.214.202.34
- 20.168.203.211
- 5.161.100.229
- 5.161.127.149
- 5.78.55.208
- 5.78.52.157
- 49.12.77.28
- 65.21.152.246
Top Ten IP Addresses Using Known Malicious User-Agents
- 80.76.51.29
- 85.31.44.203
- 185.190.24.5
- 194.169.175.135
- 194.38.20.16
- 194.169.175.22
- 194.165.17.8
- 185.190.24.91
- 5.181.86.5
- 194.165.17.27
Top Ten User-Agents Targeting Downloads Manager
These user agents are listed in descending order of tracked exploit attempts. Most of these user-agent strings are legitimate, but the bold ones appear to have been modified.
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
- Mozilla/5.0 (Linux; Android 11; ONEPLUS A6013) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Mobile Safari/537.36
- Mozilla/5.0 (iPhone; CPU iPhone OS 16_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) CriOS/107.0.5304.101 Mobile/15E148 Safari/604.1
- Mozilla/5.0 (Linux; Android 11; Lenovo YT-J706X) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
- Mozilla/5.0 (Linux; Android 12; SM-A205U) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.141 Mobile Safari/537.36
- Mozilla/5.0 (Macintosh; Intel Mac OS X 13_0_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
- Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
- Linux Mozilla
- Mozilla/5.0 (Linux; Android 12; SM-S906N Build/QP1A.190711.020; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/105.0.0.0 Mobile Safari/537.36
- Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.0.0 Safari/537.36
Top Ten Blocked Known Malicious User-Agents
While some of these user-agent strings may have been legitimate at some point, older user-agents are often used for malicious purposes.
- Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36
- wp_is_mobile
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
- Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0
- ALittle Client
- Mozilla/5.0 (X11; Ubuntu; Linux i686; rv:28.0) Gecko/20100101 Firefox/28.0
- Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)
- Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0
- Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Mobile Safari/537.36
- Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36 X-Middleton/1
Conclusion
Spikes in exploit and other attack attempts are common around holidays, as is highlighted by spikes we observed in probing attempts against the Downloads Manager plugin and blocked known malicious user-agents. These spikes occurred on or near the Christmas and New Year holidays. Fortunately for Wordfence users, firewall rules were already in place to block these attack attempts, even for Wordfence Free users. In addition to having a firewall and malware scanning in place, it is also important to ensure that all components of a website are updated with the latest security releases, and vulnerable plugins with no updates should be removed.
The Wordfence firewall protects Wordfence Premium, Care, and Response, and Free users from these vulnerabilities and attacks. Nonetheless, we strongly recommend removing or replacing the Downloads Manager plugin, as soon as possible.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both of these products include hands-on support in case you need further assistance. If you have any friends or colleagues who are using this plugin, please share this post with them and encourage them to remove or replace Downloads Manager as soon as possible.
The post Holiday Attack Spikes Target Ancient Vulnerabilities and Hidden Webshells appeared first on Wordfence.