🦸 👻 Calling all superheroes and haunters! Introducing the Cybersecurity Month Spooktacular Haunt and the WordPress Superhero Challenge for the Wordfence Bug Bounty Program! Through November 11th, 2024:
- All in-scope vulnerability types for WordPress plugins/themes with >= 1,000 active installations are in-scope for ALL researchers
- Top-tier researchers earn automatic bonuses of between 10% to 120% for valid submissions
- Pending report limits are increased for all
- It’s possible to earn up to $31,200 for high impact vulnerabilities!
On October 23rd, 2024, we received a submission for an Arbitrary File Upload vulnerability in AI Power: Complete AI Pack, a WordPress plugin with more than 10,000 active installations. This vulnerability makes it possible for an unauthenticated attacker to upload arbitrary files to a vulnerable site and achieve remote code execution.
Props to vgo0 who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $650.00 for this discovery. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Malicious File Upload protection.
We contacted the AI Power team on October 25, 2024, and received a response on the same day. After providing full disclosure details, the developer released a patch on October 26, 2024. We would like to commend the AI Power team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of AI Power: Complete AI Pack, version 1.8.90 at the time of this writing, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: AI Power: Complete AI Pack
Plugin Slug: gpt3-ai-content-generator
Affected Versions: <= 1.8.89
CVE ID: CVE-2024-10392
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: vgo0
Fully Patched Version: 1.8.90
Bounty Award: $650.00
The AI Power: Complete AI Pack plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the ‘handle_image_upload’ function in all versions up to, and including, 1.8.89. This makes it possible for unauthenticated attackers to upload arbitrary files on the affected site’s server which may make remote code execution possible.
Technical Analysis
AI Power is a WordPress plugin for AI integration with many features and functions.
Examining the code reveals that the plugin uses the handle_image_upload() function in the WPAICG_Chat class to handle image uploads in chats with GPT-4 models.
public function handle_image_upload($image) {
$wpaicg_user_uploads = get_option('wpaicg_user_uploads', 'filesystem');
$wpaicg_img_processing_method = get_option('wpaicg_img_processing_method', 'url'); // Fetch user preference
$wpaicg_delete_image = get_option('wpaicg_delete_image', 0); // Fetch delete image preference
$result = ['url' => '', 'base64' => '']; // Initialize result variable with both keys
if ($wpaicg_user_uploads === 'filesystem') {
// Save the image to a custom folder inside the uploads directory
$upload_dir = wp_upload_dir();
$upload_path = $upload_dir['basedir'] . '/wpaicg_user_uploads/';
// Create the directory if it doesn't exist
if (!file_exists($upload_path)) {
mkdir($upload_path, 0755, true);
}
$file_path = $upload_path . basename($image['name']);
// Move the uploaded file to the new location
if (move_uploaded_file($image['tmp_name'], $file_path)) {
This function checks the plugin setting to determine where the file should be saved. If ‘filesystem’ is set, which is the default value, it uploads the file to the WordPress uploads directory using the move_uploaded_file() function.
Unfortunately, the function does not include any file type or extension checks in the vulnerable version. This means that not only image files can be uploaded, but it is also possible to upload files with a .php extension. The file is uploaded to the WordPress uploads folder, which is publicly accessible by default. This makes it possible for unauthenticated attackers to upload arbitrary malicious PHP code and then access the file to trigger remote code execution on the server.
As with all arbitrary file upload vulnerabilities, this can lead to complete site compromise through the use of webshells and other techniques.
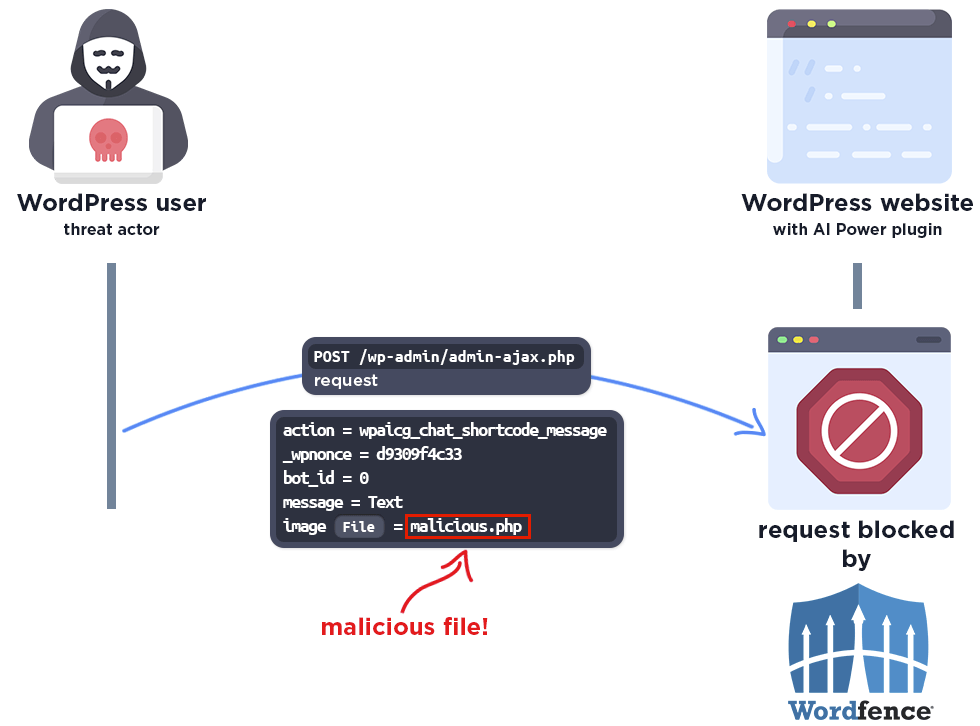
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The firewall also blocks access to the php file:
Please note this protection only works if the “Disable Code Execution for Uploads directory” option is enabled in the Wordfence Global Options page. We strongly recommend all Wordfence users enable this option.
Disclosure Timeline
October 23, 2024 – We received the submission for the Arbitrary File Upload vulnerability in AI Power: Complete AI Pack via the Wordfence Bug Bounty Program.
October 25, 2024 – We validated the report and confirmed the proof-of-concept exploit.
October 25, 2024 – We initiated contact via the vendor contact form, asking that they confirm the inbox for handling the discussion.
October 25, 2024 – The vendor confirmed the inbox for handling the discussion.
October 26, 2024 – We sent over the full disclosure details to the vendor. The vendor acknowledged the report and began working on a fix.
October 26, 2024 – The fully patched version of the plugin, 1.8.90, was released.
Conclusion
In this blog post, we detailed an Arbitrary File Upload vulnerability within the AI Power: Complete AI Pack plugin affecting versions 1.8.89 and earlier. This vulnerability allows unauthenticated threat actors to execute malicious code on the server. The vulnerability has been addressed in version 1.8.90 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of AI Power: Complete AI Pack as soon as possible considering the critical nature of this vulnerability.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post 10,000 WordPress Sites Affected by Arbitrary File Upload Vulnerability in AI Power: Complete AI Pack WordPress Plugin appeared first on Wordfence.