On February 1st, 2024, during our Bug Bounty Extravaganza, we received a submission for an Arbitrary File Upload vulnerability in Management App for WooCommerce, a WordPress plugin with 1,000+ active installations. This vulnerability makes it possible for authenticated users such as subscribers and customers to upload arbitrary files to a vulnerable site and achieve remote code execution.
Props to Lucio Sá who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $657.00 for this discovery during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on February 2, 2024. Sites using the free version of Wordfence received the same protection on March 3, 2024.
We contacted the WEmanage Team on February 2, 2024. After not receiving a reply we escalated the issue to the WordPress.org Security Team on March 8, 2024. After that, the developer released a patch on March 24, 2024.
We urge users to update their sites with the latest patched version of Management App for WooCommerce, version 1.2.3 at the time of this writing, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Management App for WooCommerce – Order notifications, Order management, Lead management, Uptime Monitoring
Plugin Slug: wemanage-app-worker
Affected Versions: <= 1.2.2
CVE ID: CVE-2024-1205
CVSS Score: 8.8 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Lucio Sá
Fully Patched Version: 1.2.3
Bounty Award: $657.00
The Management App for WooCommerce – Order notifications, Order management, Lead management, Uptime Monitoring plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the nouvello_upload_csv_file function in all versions up to, and including, 1.2.2. This makes it possible for authenticated attackers, with subscriber-level access and above, to upload arbitrary files on the affected site’s server which may make remote code execution possible.
Technical Analysis
Management App for WooCommerce, also known as WEmanage App Worker, is a WordPress plugin, which connects WooCommerce with the WEmanage app, and includes many features and functions.
Unfortunately, insecure implementation of the plugin’s CSV file upload functionality allows for arbitrary file uploads. Examining the code reveals that the permission check for the CSV file upload REST API endpoint registration only checks that the user is logged in. This means that any logged in user, such as a subscriber, can access this REST API endpoint.
register_rest_route(
$this->namespace,
'upload-csv-file',
array(
'methods' => 'POST',
'callback' => array( nouvello_wemanage_worker()->wc_api_functions, 'nouvello_upload_csv_file' ),
'permission_callback' => function( $request ) {
return is_user_logged_in();
},
)
);
The corresponding nouvello_upload_csv_file() function is used for the upload and processing of CSV files.
public function nouvello_upload_csv_file($data)
{
$body = $data->get_body();
$body_array = json_decode($body, true);
$body_json_data = $body_array[0]['json_data'];
$body_array_data = json_decode($body_json_data, true);
$csv_data = $body_array_data['file_data'];
$csv_nm = $body_array_data['file_nm'];
$csv_label = $body_array_data['csv_label'];
$ext = end(explode('.', $csv_nm));
$fn_name = time() . '.' . $ext;
$wp_upload_dir = wp_upload_dir();
$filepath_nm = $wp_upload_dir['path'] . $fn_name;
$f = fopen($filepath_nm, 'a');
fputcsv($f, $csv_label);
foreach ($csv_data as $csv_inner) :
fputcsv($f, $csv_inner);
endforeach;
fclose($f);
$result = array(
'file_path' => $filepath_nm,
'file_nm' => $csv_nm,
);
return json_encode($result);
}
Unfortunately, the file_nm parameter is not only used to specify the file name but also allows determining its file extension in vulnerable versions. This means that a PHP file extension can be specified, and PHP code can be added in the file content. This makes it possible for attackers to upload arbitrary malicious PHP code and then access the file to trigger remote code execution on the server.
Wordfence Firewall
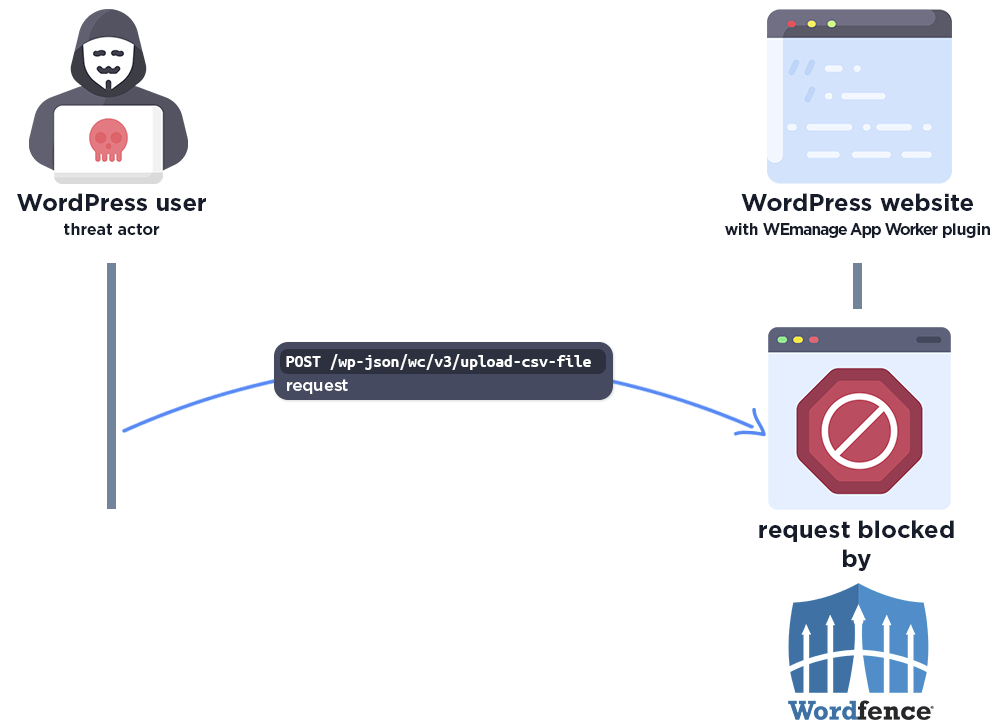
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious REST API action and blocks the request if it does not come from an existing authorized administrator.
Disclosure Timeline
February 1, 2024 – We receive the submission of the Arbitrary File Upload vulnerability in Management App for WooCommerce via the Wordfence Bug Bounty Program.
February 2, 2024 – We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
February 2, 2024 – Wordfence Premium, Care, and Response users receive a firewall rule to provide protection against any exploits that may target this vulnerability.
February 21, 2024 – We do not receive a response from the plugin developer and send a follow-up contact.
March 3, 2024 – Our firewall rule is made available to Wordfence Free users.
March 8, 2024 – We escalate the vulnerability to the WordPress.org Security Team and send over the full disclosure details.
March 24, 2024 – The fully patched version of the plugin, 1.2.3, is released.
Conclusion
In this blog post, we detailed an Arbitrary File Upload vulnerability within the Management App for WooCommerce plugin affecting versions 1.2.2 and earlier. This vulnerability allows authenticated threat actors, with minimal permissions, to execute malicious code on the server. The vulnerability has been addressed in version 1.2.3 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Management App for WooCommerce.
Wordfence users running Wordfence Premium, Wordfence Care, and Wordfence Response have been protected against these vulnerabilities as of February 2, 2024. Users using the free version of Wordfence received the same protection on March 3, 2024.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post $657 Bounty Awarded for Arbitrary File Upload Patched in WEmanage App Worker WordPress Plugin appeared first on Wordfence.