🎉 Did you know we’re running a Bug Bounty Extravaganza again?
Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through May 27th, 2024 when you opt to have Wordfence handle responsible disclosure!
On April 22th, 2024, during our second Bug Bounty Extravaganza, we received a submission for a Reflected Cross-Site Scripting (XSS) vulnerability in Yoast SEO, a WordPress plugin with more than 5 million active installations. This vulnerability makes it possible for an unauthenticated attacker to craft a request that contains malicious JavaScript. If the attacker is able to trick a site administrator into performing an action, the malicious JavaScript executes, making it possible for the attacker to create new admin users, redirect victims, or engage in other harmful attacks.
Props to Bassem Essam who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $563.00 for this discovery during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Cross-Site Scripting protection.
We contacted the Yoast team on April 23, 2024, and received a response on the same day. After providing full disclosure details, the developer released a patch on April 30, 2024. We would like to commend the Yoast team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of Yoast SEO, which is version 22.6, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Yoast SEO
Plugin Slug: wordpress-seo
Affected Versions: <= 22.5
CVE ID: CVE-2024-4041
CVSS Score: 6.1 (Medium)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Researcher/s: Bassem Essam
Fully Patched Version: 22.6
Bounty Awarded: $563.00
The Yoast SEO plugin for WordPress is vulnerable to Reflected Cross-Site Scripting via URLs in all versions up to, and including, 22.5 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link.
Technical Analysis
The Yoast SEO plugin is the most popular search engine optimization WordPress plugin, which includes many features and functions.
The plugin uses the add_premium_link() function in the WPSEO_Admin_Bar_Menu class to add a premium promotion link to the WordPress admin bar.
protected function add_premium_link( WP_Admin_Bar $wp_admin_bar ) {
$sale_percentage = '';
if ( YoastSEO()->classes->get( Promotion_Manager::class )->is( 'black-friday-2023-promotion' ) ) {
$sale_percentage = sprintf(
'<span class="admin-bar-premium-promotion">%1$s</span>',
__( '-30%', 'wordpress-seo' )
);
}
$wp_admin_bar->add_menu(
[
'parent' => self::MENU_IDENTIFIER,
'id' => 'wpseo-get-premium',
// Circumvent an issue in the WP admin bar API in order to pass `data` attributes. See https://core.trac.wordpress.org/ticket/38636.
'title' => sprintf(
'<a href="%1$s" target="_blank" data-action="load-nfd-ctb" data-ctb-id="f6a84663-465f-4cb5-8ba5-f7a6d72224b2" style="padding:0;" rel="noopener">%2$s » %3$s</a>',
$this->shortlinker->build_shortlink( 'https://yoa.st/admin-bar-get-premium' ),
__( 'Get Yoast SEO Premium', 'wordpress-seo' ),
$sale_percentage
),
'meta' => [
'tabindex' => '0',
],
]
);
}
Examining the code reveals that the escape is missing at the shortlinker build_shortlink() function, which returns the link’s value.
public function build_shortlink( $url ) {
return YoastSEO()->helpers->short_link->build( $url );
}
The build_shortlink() function in the WPSEO_Shortlinker class calls the build() function from the Short_Link_Helper class.
public function build( $url ) {
return add_query_arg( $this->collect_additional_shortlink_data(), $url );
}
The build() function from the Short_Link_Helper class adds to $url the values retrieved from the collect_additional_shortlink_data() function.
protected function collect_additional_shortlink_data() {
$data = [
'php_version' => $this->get_php_version(),
'platform' => 'wordpress',
'platform_version' => $this->get_platform_version(),
'software' => $this->get_software(),
'software_version' => WPSEO_VERSION,
'days_active' => $this->get_days_active(),
'user_language' => get_user_locale(),
];
// phpcs:ignore WordPress.Security.NonceVerification.Recommended -- Reason: We are not processing form information.
if ( isset( $_GET['page'] ) && is_string( $_GET['page'] ) ) {
// phpcs:ignore WordPress.Security.NonceVerification.Recommended -- Reason: We are not processing form information.
$admin_page = sanitize_text_field( wp_unslash( $_GET['page'] ) );
if ( ! empty( $admin_page ) ) {
$data['screen'] = $admin_page;
}
}
return $data;
}
The code reveals that among the additional values appended to the URL, the ‘screen’ data is defined based on the ‘page’ GET input value. This makes it possible for an attacker to supply a malicious payload through the ‘page’ parameter that will then execute when a user hovers over the Yoast logo in the admin menu bar.
As with any Cross-Site Scripting vulnerability, this can be exploited to perform several actions like creating new administrative user accounts, injecting theme and plugin files with backdoors, and redirecting visitors to malicious sites, all of which can be used for complete site takeover. This vulnerability requires users to click on a link in order to be successful, and is a reminder for site administrators and users to follow security best practices and avoid clicking on links from untrusted sources.
Wordfence Firewall
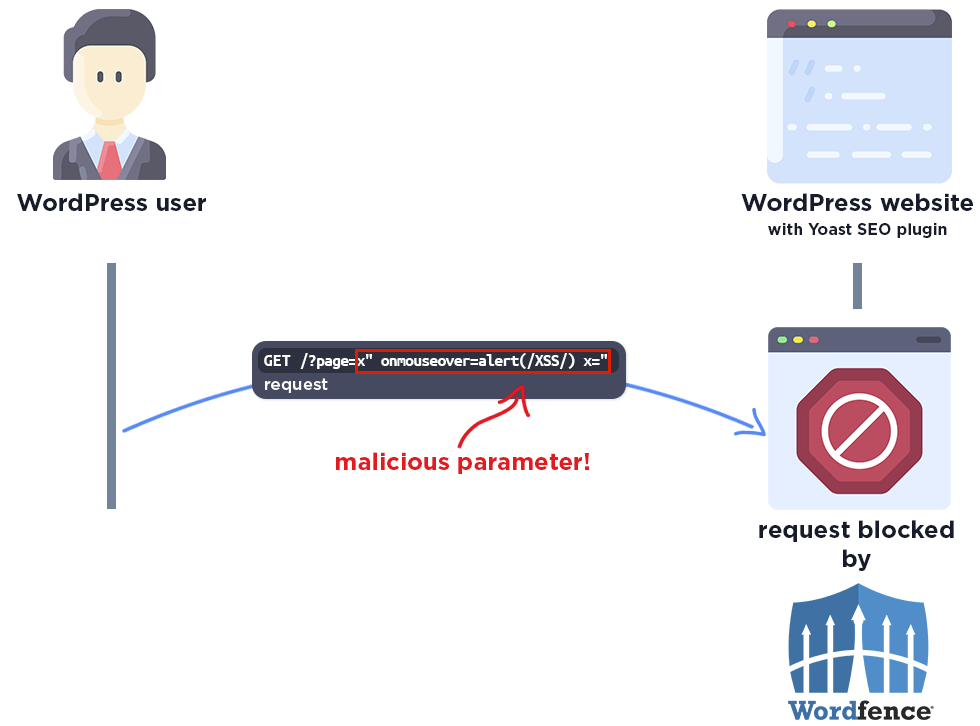
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The attacker needs to send a malicious link to the administrator for the exploit.
The Wordfence firewall rule detects the malicious parameter and blocks the request.
Disclosure Timeline
April 22, 2024 – We receive the submission of the Reflected Cross-Site Scripting (XSS) vulnerability in Yoast SEO via the Wordfence Bug Bounty Program.
April 22, 2024 – We validate the report and confirm the proof-of-concept exploit.
April 23, 2024 – We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
April 23, 2024 – The vendor confirms the inbox for handling the discussion.
April 26, 2024 – We send over the full disclosure details.
April 28, 2024 – The vendor acknowledges the report and begins working on a fix.
April 30, 2024 – The fully patched version of the plugin, 22.6, is released.
Conclusion
In this blog post, we detailed a Reflected Cross-Site Scripting (XSS) vulnerability within the Yoast SEO plugin affecting versions 22.5 and earlier. This vulnerability allows unauthenticated threat actors to inject malicious web scripts into pages that execute when a user accesses an affected page. The vulnerability has been fully addressed in version 22.6 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Yoast SEO.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post $563 Bounty Awarded for Reflected Cross-Site Scripting Vulnerability Patched in Yoast SEO WordPress Plugin appeared first on Wordfence.