📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors? Through October 14th, researchers can earn up to $31,200, for all in-scope vulnerabilities submitted to our Bug Bounty Program! Find a vulnerability, submit the details directly to us, and we handle all the rest.
On July 24th, 2024, we received a submission for a Remote Code Execution via Race Condition vulnerability in Bit File Manager, a WordPress plugin with more than 20,000 active installations. This vulnerability can be leveraged to execute code remotely.
Props to TANG Cheuk Hei (siunam) who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $358.00 for this discovery. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on August 9, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on September 8, 2024.
We provided full disclosure details to the Bit Apps team on August 14, 2024. The developer released a patch on August 21, 2024. We would like to commend the Bit Apps team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of Bit File Manager, version 6.5.6 at the time of this writing, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Bit File Manager – 100% Free & Open Source File Manager and Code Editor for WordPress
Plugin Slug: file-manager
Affected Versions: 6.0 – 6.5.5
CVE ID: CVE-2024-7627
CVSS Score: 8.1 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: TANG Cheuk Hei (siunam)
Fully Patched Version: 6.5.6
Bounty Award: $358.00
The Bit File Manager plugin for WordPress is vulnerable to Remote Code Execution in versions 6.0 to 6.5.5 via the ‘checkSyntax’ function. This is due to writing a temporary file to a publicly accessible directory before performing file validation. This makes it possible for unauthenticated attackers to execute code on the server if an administrator has allowed Guest User read permissions.
Technical Analysis
The Bit File Manager is a WordPress plugin that, in addition to being primarily a file manager, also includes a code editor. The unique feature of the plugin is that it can be made accessible to guests through a setting, allowing them to view the list of files in the folder and download them.
Examining the code reveals that the plugin uses the validate() function in the FileEditValidator class to check the syntax of PHP code it receives via a parameter.
public function validate($cmd, &$args, $elfinder, $volume)
{
try {
$this->checkPermission();
} catch (PreCommandException $th) {
return $th->getError();
}
$args['content'] = stripcslashes($args['content']); // Default wordpress slashing removed.
// Checking syntax for PHP file.
if (strpos($args['content'], '<?php') !== false) {
try {
$this->checkSyntax($args['content']);
} catch (PreCommandException $th) {
return $th->getError();
}
}
}
Unfortunately, unauthenticated attackers can access this syntax check feature due to improper permission checks, caused by a faulty variable type check in an if statement.
The checkPermission() function in the FileEditValidator class includes a constant value check and a permission check.
private function checkPermission()
{
$error = '';
if (defined('DISALLOW_FILE_EDIT') && DISALLOW_FILE_EDIT) {
$error = __('File edit is disabled. To allow edit, please set DISALLOW_FILE_EDIT to false in wp-config file', 'file-manager');
}
if (is_null($error) && !Plugin::instance()->permissions()->currentUserCanRun('edit')) {
$error = __('Not Authorized to edit file', 'file-manager');
}
if (!empty($error)) {
throw new PreCommandException(esc_html($error));
}
}
The variable $error is initialized to an empty string and at no point in the function changed to null. Thus, it cannot be null when the permissions check is reached. The is_null() condition within the if statement will always return false, meaning the permission check is never validated.
After the permission check, the plugin uses the checkSyntax() function in the FileEditValidator class to check the syntax.
public function checkSyntax($content)
{
$error = '';
if (!function_exists('exec')) {
$error = __('exec() is required for php syntax check');
} else {
$tempFilePath = FM_UPLOAD_BASE_DIR . 'temp.php';
$fp = fopen($tempFilePath, 'w+');
fwrite($fp, $content);
fclose($fp);
exec('php -l ' . escapeshellarg($tempFilePath), $output, $return);
$errorMessages = [];
foreach ($output as $result) {
if (
strpos($result, 'No syntax errors detected') !== false
|| $result == ''
) {
continue;
}
if (strpos($result, 'Errors parsing') !== false) {
$error = wp_sprintf(
// translators: 1: Temporary file path
__('Errors parsing the file [ %s ] as php script', 'file-manager'),
str_replace('temp', '', $tempFilePath)
);
} else {
$errorMessages[] = $result;
}
}
unlink($tempFilePath);
To perform a syntax check, a file-managertemp.php file with the specified content is uploaded to the WordPress uploads folder, which is publicly accessible. This makes it possible for attackers to upload arbitrary malicious PHP code and then access the file to trigger remote code execution on the server. As with all remote code execution vulnerabilities, this can lead to complete site compromise through the use of webshells and other techniques.
It’s important to note that the file is immediately deleted from the server within the checkSyntax() function using the unlink() function, but the attacker can successfully exploit the vulnerability by continuously sending requests to the PHP temp file and attempting to access it for execution, taking advantage of a race condition. The researcher was able to successfully demonstrate an exploit that could easily be replicated across environments with relatively consistent success.
The complete exploit process looks like this:
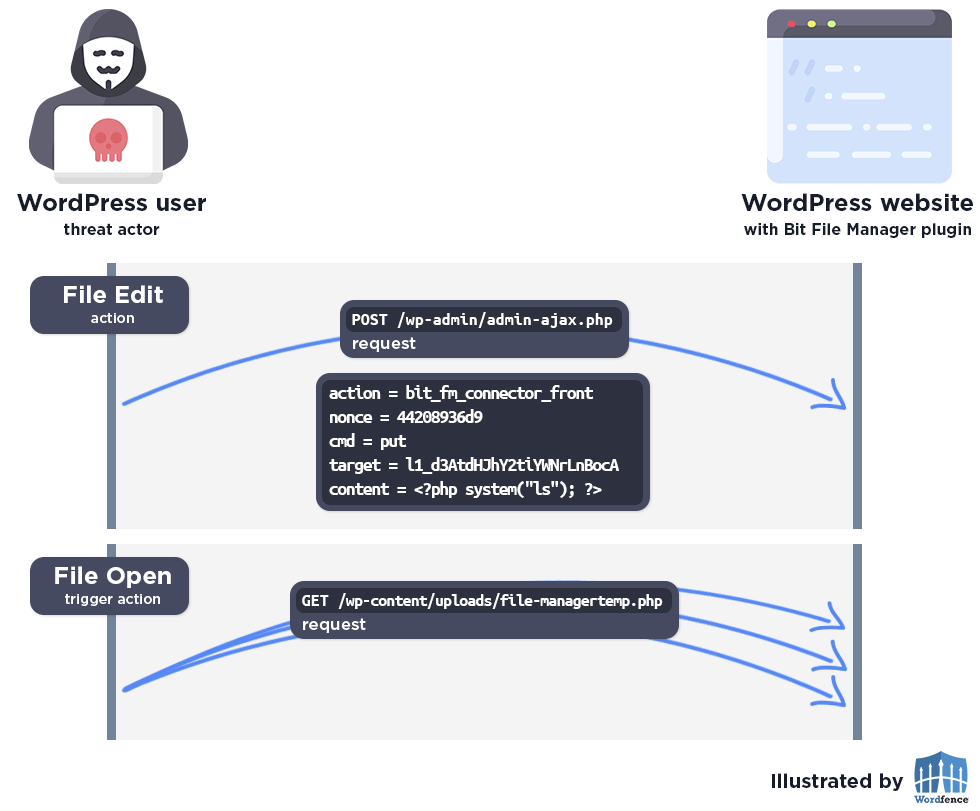
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
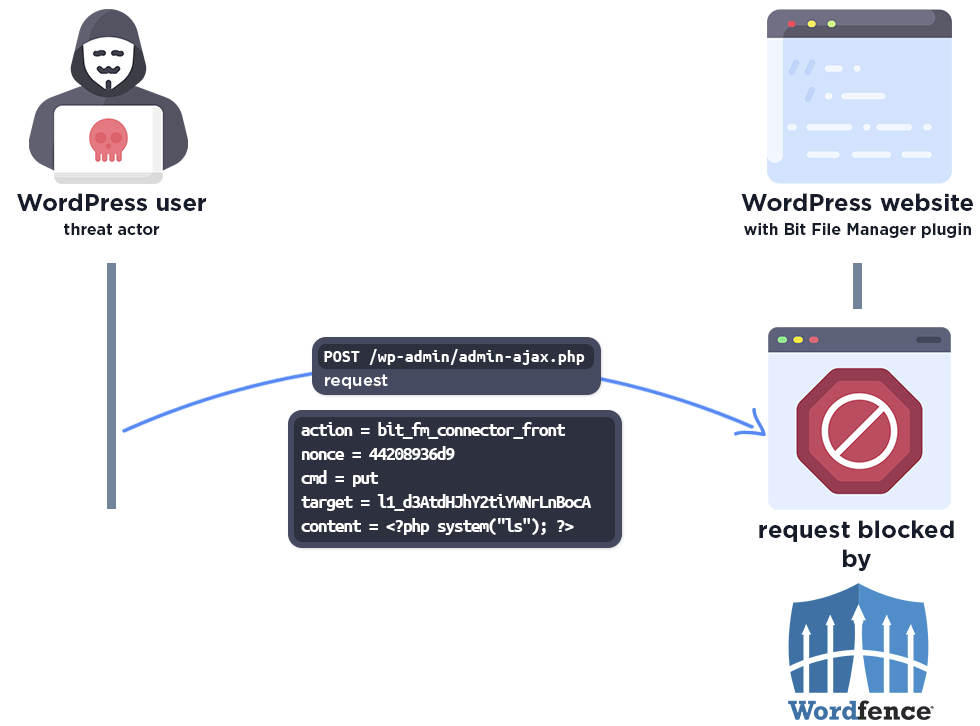
The firewall also blocks access to the temp file:

Please note this protection only works if the “Disable Code Execution for Uploads directory” option is enabled in the Wordfence Global Options page. We strongly recommend all Wordfence users enable this option.
Disclosure Timeline
July 24, 2024 – We received the submission for the Remote Code Execution via Race Condition vulnerability in Bit File Manager via the Wordfence Bug Bounty Program.
August 8, 2024 – We validated the report and confirmed the proof-of-concept exploit.
August 9, 2024 – Wordfence Premium, Care, and Response users received a firewall rule to provide protection against any exploits that may target this vulnerability.
August 14, 2024 – We sent over the full disclosure details to the vendor.
August 14, 2024 – The vendor acknowledged the report and began working on a fix.
August 21, 2024 – The fully patched version of the plugin, 6.5.6, is released.
September 8, 2024 – Wordfence Free users will receive the same protection.
Conclusion
In this blog post, we detailed a Remote Code Execution via Race Condition vulnerability within the Bit File Manager plugin affecting versions 6.0 through 6.5.5. This vulnerability allows unauthenticated threat actors to execute malicious code on the server. The vulnerability has been addressed in version 6.5.6 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Bit File Manager as soon as possible considering the critical nature of this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on August 9, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on September 8, 2024.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post 20,000 WordPress Sites Affected by Remote Code Execution Vulnerability in Bit File Manager WordPress Plugin appeared first on Wordfence.



