🎉 Did you know we’re running a Bug Bounty Extravaganza again?
Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through May 27th, 2024 when you opt to have Wordfence handle responsible disclosure!
On March 25th, 2024, during our second Bug Bounty Extravaganza, we received a submission for an unauthenticated SQL Injection vulnerability in Email Subscribers by Icegram Express, a WordPress plugin with more than 90,000 active installations. This vulnerability can be leveraged to extract sensitive data from the database, such as password hashes.
Props to Arkadiusz Hydzik who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $1,250.00 for this discovery during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in SQL Injection protection.
We contacted the Icegram Team regarding a separate vulnerability on March 21, 2024, and received a response on the same day. After providing full disclosure details about this vulnerability on March 25, 2024, the developer released a patch on March 27, 2024. We would like to commend the Icegram Team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of Email Subscribers by Icegram Express, which is version 5.7.15, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Email Subscribers by Icegram Express – Email Marketing, Newsletters, Automation for WordPress & WooCommerce
Plugin Slug: email-subscribers
Affected Versions: <= 5.7.14
CVE ID: CVE-2024-2876
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Arkadiusz Hydzik
Fully Patched Version: 5.7.15
Bounty Award: $1,250.00
The Email Subscribers by Icegram Express – Email Marketing, Newsletters, Automation for WordPress & WooCommerce plugin for WordPress is vulnerable to SQL Injection via the ‘run’ function of the ‘IG_ES_Subscribers_Query’ class in all versions up to, and including, 5.7.14 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database.
Technical Analysis
Icegram Express is a WordPress plugin for email marketing, managing email subscribers, and sending newsletters.
Unfortunately, insecure implementation of the plugin’s subscribers query functionality allows for SQL injection. Examining the code reveals that the plugin adds the maybe_apply_bulk_actions_on_all_contacts() function in the Email_Subscribers_Admin class to the admin init hook. Since this function does not perform a nonce and capability check, it can also be called by unauthenticated attackers.
add_action( 'admin_init', array( $this, 'maybe_apply_bulk_actions_on_all_contacts' ) );
This function queries the subscribers from the database using the IG_ES_Subscribers_Query class. The run() function that queries the database contains the following code snippets:
if ( ! empty( $this->args['conditions'] ) ) {
foreach ( $this->args['conditions'] as $i => $and_conditions ) {
$sub_cond = array();
if ( ! empty( $and_conditions ) ) {
foreach ( $and_conditions as $j => $condition ) {
$field = isset( $condition['field'] ) ? $condition['field'] : ( isset( $condition[0] ) ? $condition[0] : null );
$operator = isset( $condition['operator'] ) ? $condition['operator'] : ( isset( $condition[1] ) ? $condition[1] : null );
$value = isset( $condition['value'] ) ? $condition['value'] : ( isset( $condition[2] ) ? $condition[2] : null );
The function builds a complex query. In such a case escaping the parameters with the esc_sql() function would be a suitable solution, but unfortunately this is missing in the vulnerable version.
$joins[] = "LEFT JOIN {$wpbd->prefix}ig_links AS {$alias}{$field} ON {$alias}{$field}.link IN ('" . implode( "','", $value ) . "')";
The JOIN statement is added to the query without the WordPress wpdb prepare() function. The prepare() function would parameterize and escape the SQL query for safe execution in WordPress, thereby providing protection against SQL injection attacks.
Since UNION-Based SQL injection is not possible due to the structure of the query, an attacker would need to use a time-based blind approach to extract information from the database. This means that they would need to use SQL CASE statements along with the SLEEP() command while observing the response time of each request to steal information from the database. This is an intricate, yet frequently successful method to obtain information from a database when exploiting SQL Injection vulnerabilities.
Wordfence Firewall
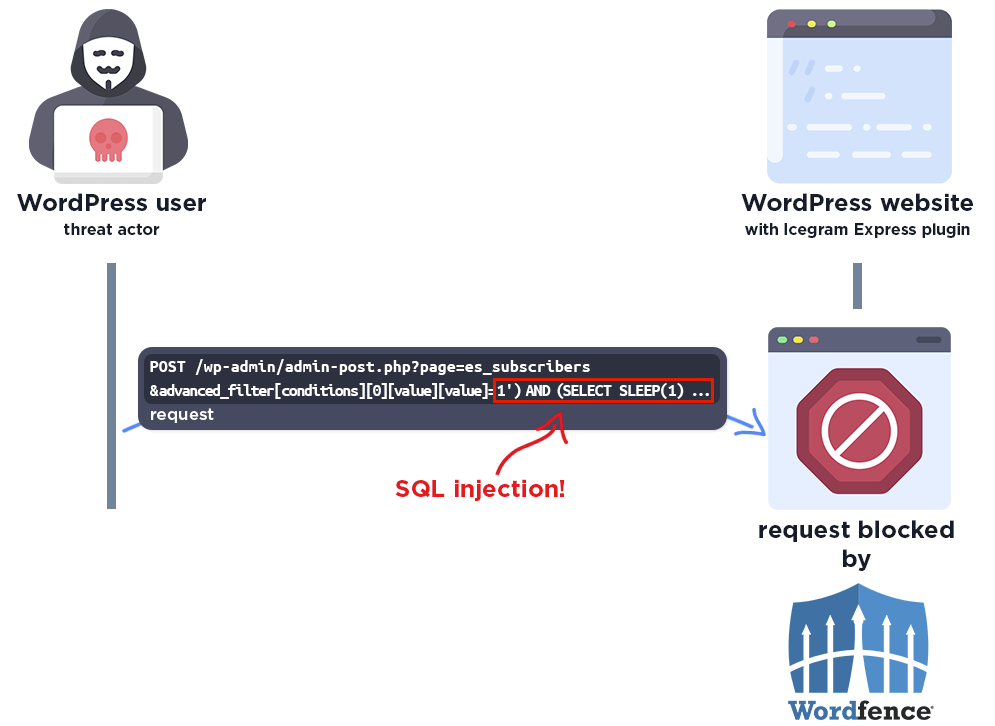
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious SQL query and blocks the request.
Disclosure Timeline
March 24, 2024 – We receive the submission of the SQL Injection vulnerability in Email Subscribers by Icegram Express via the Wordfence Bug Bounty Program.
March 25, 2024 – We validate the report and confirm the proof-of-concept exploit.
March 25, 2024 – We send over the full disclosure details. The vendor acknowledges the report and begins working on a fix.
March 27, 2024 – The fully patched version of the plugin, 5.7.15, is released.
Conclusion
In this blog post, we detailed a SQL Injection vulnerability within the Email Subscribers by Icegram Express plugin affecting versions 5.7.14 and earlier. This vulnerability allows unauthenticated threat actors to inject malicious SQL queries to steal sensitive information from the database. The vulnerability has been fully addressed in version 5.7.15 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Email Subscribers by Icegram Express.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post $1,250 Bounty Awarded for Unauthenticated SQL Injection Vulnerability Patched in Email Subscribers by Icegram Express WordPress Plugin appeared first on Wordfence.