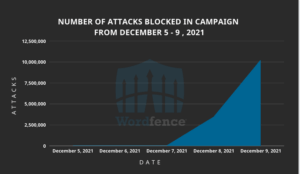
Today, on December 9, 2021, our Threat Intelligence team noticed a drastic uptick in attacks targeting vulnerabilities that make it possible for attackers to update arbitrary options on vulnerable sites. This led us into an investigation which uncovered an active attack targeting over a million WordPress sites. Over the past 36 hours, the Wordfence network has blocked over 13.7 million attacks targeting four different plugins and several Epsilon Framework themes across over 1.6 million sites and originating from over 16,000 different IP addresses.
Wordfence Premium Users are protected against any exploit attempts targeting all of these vulnerabilities. Wordfence free users are protected against attacks targeting all of the vulnerabilities except for the recently disclosed vulnerability in PublishPress Capabilities. Wordfence Premium users received a firewall rule for the Unauthenticated Arbitrary Options Update vulnerability in PublishPress Capabilities on December 6th, 2021, and sites still running the free version of Wordfence will receive the firewall rule on January 6, 2021.
A Closer Look at the Attack Data
Attackers are targeting 4 individual plugins with Unauthenticated Arbitrary Options Update Vulnerabilities. The four plugins consist of Kiwi Social Share, which has been patched since November 12, 2018, WordPress Automatic and Pinterest Automatic which have been patched since August 23, 2021, and PublishPress Capabilities which was recently patched on December 6, 2021. In addition, they are targeting a Function Injection vulnerability in various Epsilon Framework themes in an attempt to update arbitrary options.
In most cases, the attackers are updating the users_can_register option to enabled and setting the default_role option to `administrator.` This makes it possible for attackers to register on any site as an administrator effectively taking over the site.
Our attack data indicates that there was very little activity from attackers targeting any of these vulnerabilities until December 8, 2021. This leads us to believe that the recently patched vulnerability in PublishPress Capabilities may have sparked attackers to target various Arbitrary Options Update vulnerabilities as part of a massive campaign.
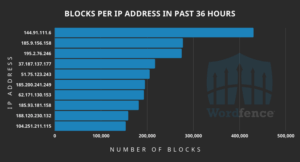
The top 10 offending IPs over the past 36 hours include:
- 144.91.111.6 with 430,067 attacks blocked.
- 185.9.156.158 with 277,111 attacks blocked.
- 195.2.76.246 with 274,574 attacks blocked.
- 37.187.137.177 with 216,888 attacks blocked.
- 51.75.123.243 with 205,143 attacks blocked.
- 185.200.241.249 with 194,979 attacks blocked.
- 62.171.130.153 with 192,778 attacks blocked.
- 185.93.181.158 with 181,508 attacks blocked.
- 188.120.230.132 with 158,873 attacks blocked.
- 104.251.211.115 with 153,350 attacks blocked.
How Can I Keep My Site Protected?
Due to the severity of these vulnerabilities and the massive campaign targeting them, it is incredibly important to ensure your site is protected from compromise. If your site is running Wordfence Premium then it is already protected against any exploit attempts targeting any of these vulnerabilities. If your site is running the free version of Wordfence then it is protected against any exploits targeting any of the vulnerabilities, with the exception of the recently patched vulnerability in PublishPress Capabilities. Sites running Wordfence Free will receive the firewall rule for PublishPress Capabilities on January 6, 2021, which is 30 days after Wordfence Premium users.
Regardless of the protection that Wordfence provides, we strongly recommend ensuring that any sites running one of these plugins or themes has been updated to the patched version. We have the affected versions of each product outlined below. Please ensure that your sites are running a version higher than any of the ones listed. Simply updating the plugins and themes will ensure that your site stays safe from compromise against any exploits targeting these vulnerabilities.
The following are the affected plugins and their versions:
- PublishPress Capabilities <= 2.3
- Kiwi Social Plugin <= 2.0.10
- Pinterest Automatic <= 4.14.3
- WordPress Automatic <= 3.53.2
The following are the affected Epsilon Framework theme versions:
- Shapely <=1.2.8
- NewsMag <=2.4.1
- Activello <=1.4.1
- Illdy <=2.1.6
- Allegiant <=1.2.5
- Newspaper X <=1.3.1
- Pixova Lite <=2.0.6
- Brilliance <=1.2.9
- MedZone Lite <=1.2.5
- Regina Lite <=2.0.5
- Transcend <=1.1.9
- Affluent <1.1.0
- Bonkers <=1.0.5
- Antreas <=1.0.6
- NatureMag Lite – No patch known. Recommended to uninstall from site.
How Do I Know If My Site Has Been Infected and What Should I do?
As previously stated, the attackers are updating the users_can_register option to enabled and setting the default_role option to `administrator` in most cases.
To determine if a site has been compromised by these vulnerabilities, we recommend reviewing the user accounts on the site to determine if there are any unauthorized user accounts. If the site is running a vulnerable version of any of the four plugins or various themes, and there is a rogue user account present, then the site was likely compromised via one of these plugins. Please remove any detected user accounts immediately.
It is also important to review the settings of the site and ensure that they have been set back to their original state. You can find these settings by going to the http://examplesite[.]com/wp-admin/options-general.php page. Please make sure the `Membership` setting is correctly set to enabled or disabled, depending on your site, and validate that the `New User Default Role` is appropriately set. We strongly recommend not using `Administrator` for the new user default role as this can lead to inevitable site compromise.
Please review this guide to cleaning a hacked site with Wordfence to complete the clean of the site once the intrusion vector has been determined and the immediate issues have been resolved. If the entire site is not scanned and cleaned to ensure there are no additional backdoors, it may be possible for an attacker to regain access to the site.
If you would like assistance in cleaning a site compromised by one of these plugins, we recommend using our Professional Site Cleaning services to help get your site back online.
Conclusion
In today’s post, we detailed an active attack campaign targeting various plugins and themes that make it possible for attackers to effectively take over the vulnerable sites through the use of arbitrary option updating. We strongly recommend ensuring that all of your sites have been updated to the patched versions of the plugins and themes.
We also recommend that you share this post within the WordPress community to create awareness among site owners about this attack campaign and how to defend against it.
We may update this post as we receive new information.
The post 1.6 Million WordPress Sites Hit With 13.7 Million Attacks In 36 Hours From 16,000 IPs appeared first on Wordfence.



